IOC in computer forensics is an artifact observed on a network or in operating system that with high confidence indicates a computer intrusion.
Typical IOCs are virus signatures and IP addresses, MD5 hashes of malware files or URLs of botnet command and control centers.
OpenIOC stands for Open Indicators of Compromise. OpenIOC is an extensible XML schema for the description of technical characteristics that identify a known threat, an attacker’s methodology, or other evidence of compromise. OpenIOC was created by MANDIANT.
- Understanding Indicators of Compromise (IOC)
- Sharing Indicators of Compromise: An Overview of Standards and Formats
- Pros and Cons of: OpenIOC, CybOX, IODEF
- Detect, SHARE, Protect: Solutions for Improving Threat Data Exchange among CERTs, by ENISA
- Effective Management and Sharing of Indicators of Compromise
- Using IOC (Indicators of Compromise) in Malware Forensics (SANS)
- Tools and Standards for Cyber Threat Intelligence Projects
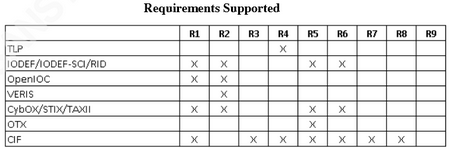
- R1 – Import/Export indicator details
R2 – Import/Export structured incident data
R5 – Capability to automate the import and export of CTI data.
R6 – authentication and confidentiality when sharing data.
- R1 – Import/Export indicator details
- IOCbucket
- shared IOCs
- Flamer IOC
-
Tools
- IOC Editor
- create, edit and compare IOC
- Redline
- Other Mandiant tools (free)
- Memoryze
- memory forensic software
- Memoryze
- IOC Editor
Cyber Observable eXpression (CybOX) is a standardized language for representing cyber observables, whether from observation in the operational cyber domain or as patterns of observables that could be observed.
- Brief Introduction to the Cyber Observables eXpression (CybOX)
- documents
- CyBOX intro
- with use cases
- Tools
- Threat Intelligence Sharing using STIX and TAXII
- including CyBOX
-
Information Sharing Specifications for Cybersecurity
from FAQ:
A4. What is the difference between “cyber observables” and “cyber indicators”?
Cyber observables are statements of fact; they capture what was observed or could be observed in the cyber operational domain.
Cyber indicators are cyber observable patterns with relevant contextual information that provide meaning and guidance around the observable patterns, such as a registry key value associated with a known bad actor or a spoofed email address used on this date and sent to these accounts on this date.
Other links
- Malware Information Sharing Platform (MISP)
- central IOC database
- correlation
- export/import
- MISP presentation
- by NATO Communications and Information Agency
- The MANTIS Cyber-Intelligence Management Framework
- The MANTIS (Model-based Analysis of Threat Intelligence Sources) Framework consists of several Django Apps that, in combination, support the management of cyber threat intelligence expressed in standards such as STIX, CybOX, OpenIOC, IODEF (RFC 5070), etc.
- Indicators of Compromise in Memory Forensics (SANS)
- Alert (TA14-212A): Backoff Point-of-Sale Malware
- contains IOCs for this alert