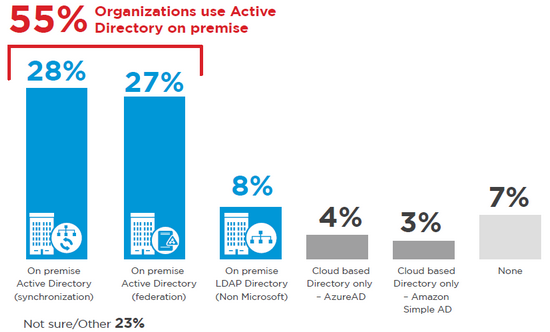
Yet another survey results are available in the “2016 Cloud Security Spotlight Report” and is interesting reading.
Example Applications
Q: Which of the following cloud applications are deployed or will be deployed in your organization?

Example Authentication
Q: What is the authoritative directory you use for identity data and authentication, and authorization of access for your cloud based applications?