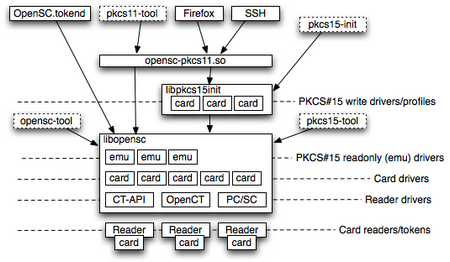
At OpenSC page:
OpenSC provides a set of libraries and utilities to work with smart cards. Its main focus is on cards that support cryptographic operations, and facilitate their use in security applications such as authentication, mail encryption and digital signatures.
OpenSC implements the PKCS#11 API.
On the card OpenSC implements the PKCS#15 standard (file structure).
Good:
- Support many smart cards
-
- National ID Cards
- Generic smart cards
-
- Cryptoflex, MyEID, STARCOS
- USB Tokens
To improve:
- Man pages are out of date
-
- Use build-in help pages
Opensc command examples
C:\Program Files\OpenSC Project\OpenSC\tools>opensc-tool --list-readers # Detected readers (pcsc) Nr. Card Features Name 0 Yes Generic Smart Card Reader Interface 0 C:\Program Files\OpenSC Project\OpenSC\tools>opensc-tool --reader 0 --atr 3b:f5:18:00:00:81:31:fe:45:4d:79:45:49:44:9a
Logging is available via -v parameter
C:\Program Files\OpenSC Project\OpenSC\tools>opensc-tool --reader 0 --name -v Connecting to card in reader Generic Smart Card Reader Interface 0... Using c ard driver MyEID cards with PKCS#15 applet. Card name: MyEID cards with PKCS#15 applet
PKCS11 examples
Retrieving information
C:\Program Files\OpenSC Project\OpenSC\tools>pkcs11-tool --module "C:\Program Files\Fujitsu Services\ActiveSecurity MyClient\Crypt
oki.dll" --show-info
Cryptoki version 2.11
Manufacturer Fujitsu Services Oy
Library mPollux DigiSign Client (ver 0.1)
Using slot 0 with a present token (0x2021880)
C:\Program Files\OpenSC Project\OpenSC\tools>pkcs11-tool --module "C:\Program Files\Fujitsu Services\ActiveSecurity MyClient\Crypt
oki.dll" --list-mechanisms
Using slot 0 with a present token (0x1fdfa70)
Supported mechanisms:
MD5, digest
SHA-1, digest
RSA-PKCS, keySize={1024,4096}, hw, encrypt, decrypt, sign, verify
MD5-RSA-PKCS, keySize={1024,4096}, hw, encrypt, decrypt, sign, verify
SHA1-RSA-PKCS, keySize={1024,4096}, hw, encrypt, decrypt, sign, verify
RSA-PKCS-KEY-PAIR-GEN, keySize={1024,4096}, hw, generate_key_pair
C:\Program Files\OpenSC Project\OpenSC\tools>pkcs11-tool --module "C:\Program Files\Fujitsu Services\ActiveSecurity MyClient\Crypt
oki.dll" --list-objects
Using slot 0 with a present token (0x20afab0)
Private Key Object; RSA
label: Encryption key [kx00]
ID: 45
Usage: decrypt, sign, unwrap
Public Key Object; RSA 1024 bits
label: Encryption key [kx00]
ID: 45
Usage: none
Certificate Object, type = X.509 cert
label: Encryption certificate for key (69) [kxc00]
ID: 45
PKCS15 examples
Erasing the MyEID card
C:\Program Files\OpenSC Project\OpenSC\tools>pkcs15-init -E -T Using reader with a card: Generic Smart Card Reader Interface 0 PIN [Security Officer PIN] required. Please enter PIN [Security Officer PIN]:
To browse PKCS15 file structure, after card was initiated with vendor tool (MyEID)
C:\Program Files\OpenSC Project\OpenSC\tools>opensc-explorer OpenSC Explorer version 0.12.2-rc1 Using reader with a card: Generic Smart Card Reader Interface 0 OpenSC [3F00]> ls FileID Type Size [5015] DF 32767 Name: \xA0\x00\x00\x00cPKCS-15 OpenSC [3F00]> info 5015 Dedicated File ID 5015 File path: 3F00/5015 File size: 32767 bytes DF name: \xA0\x00\x00\x00cPKCS-15 ACL for SELECT: N/A ACL for LOCK: N/A ACL for DELETE: NEVR ACL for CREATE: CHV3 ACL for REHABILITATE: N/A ACL for INVALIDATE: N/A ACL for LIST FILES: N/A ACL for CRYPTO: N/A ACL for DELETE SELF: N/A Proprietary attributes: 00 02 Security attributes: 33 FF FF OpenSC [3F00]> cd .. unable to go up, already in MF. OpenSC [3F00]> cd 5015 OpenSC [3F00/5015]> ls FileID Type Size OpenSC [3F00/5015]>
Other commands
opensc-tool –reader 0 –list-drivers
opensc-tool –reader 0 –serial
opensc-tool –list-algorithms
pkcs15-tool –list-keys
pkcs15-tool –list-certificates
pkcs15-tool –list-pins
pkcs15-tool –dump
Frequently asked questions
- PKCS#11 is a software API for accessing cryptographic hardware like smart cards or HSMs
- PKCS#15 is a format of on-card structures that defines a “filesystem layout” for smart cards.
Links
- Security Considerations
-
- including opensc.conf settings
- Degugging
- Installing OpenSC and initializing the smartcard
-
- with steps and environment variable setting, erase and initialize command and warning of loosing private key, if stored only on smart card