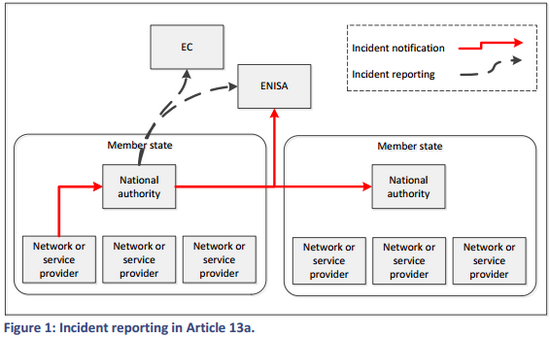
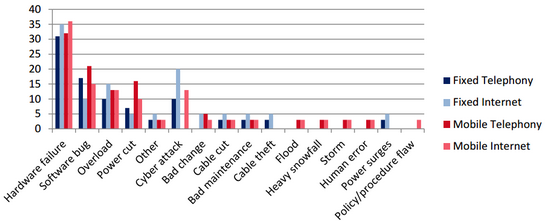
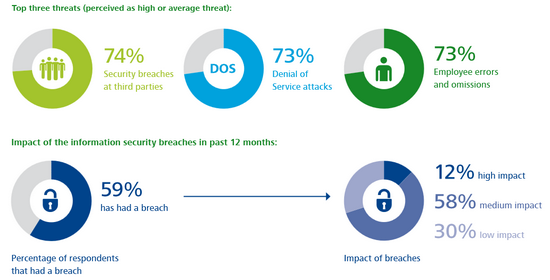
It is a common mistake is to send an email to someone without intention. For example, by quickly replying to an internal email without realizing that there were external recipients included in the distribution list.
This blog is about avoiding sending emails to external email addresses by a mistake.
In the Microsoft Outlook, there are some client side settings which might help to prevent those mistakes: rules for incoming and outgoing emails, and email categories to visualize external emails to the user.
The figure below shows an example:
- ellipse 1: incoming email list shows External category for all received emails which come from external or has external recipients. This is done by 2 rules: “Email from External” and “Email with External recipients“
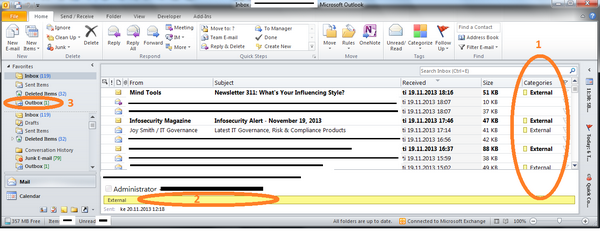
- ellipse 2: Category External is visible in the reading pane as well.
- ellipse 3: Emails send with External recipients will stay in the Outbox for 5 minutes. This is done by rule “Email send to External“. The 5 min delay can be avoided if the user specifically assign category “Send Now” for the email.
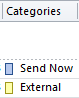
Categories External and “Send Now”
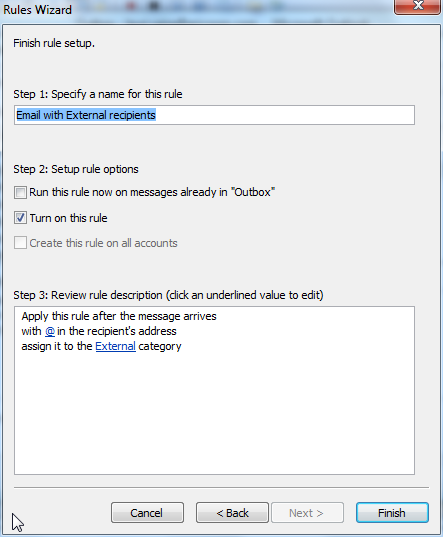
Rule: Email from External
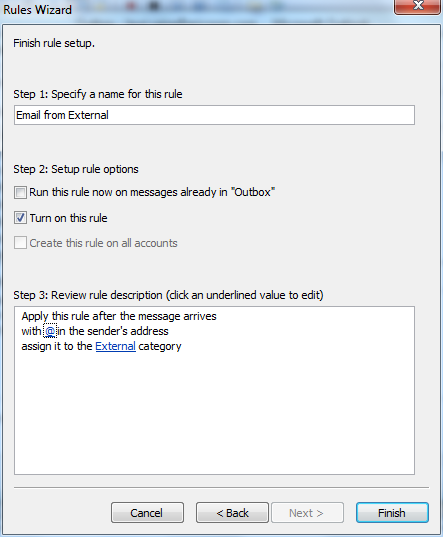
Rule: Email with External recipients
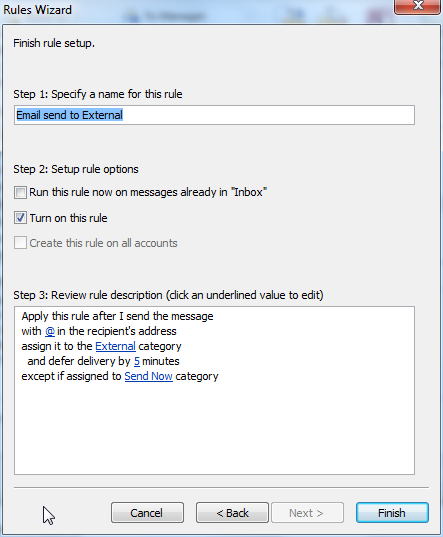
Rule: Email send to External
This rule will delay the email sending for 5 minutes. During that time the email is kept in the Outbox. Therefore it is practical to include also the Outbox in the Favorites to make it visible to the user.
More Information
These rules are using the fact, that in the Microsoft Outlook, internal email addresses do not contain “@” character. Naturally there are many other adaptations possible in the rules.
Note, custom actions like preventing the sending of the email in certain conditions requires some 3pp tool or programming.