Ponemon Institute has created a report, commissioned by Tripwire, about the cost of compliance. This is good material to look for any security manager.
Ponemon Institute and Tripwire Inc. conducted The True Cost of Compliance research to determine the full costs associated with an organization’s compliance efforts. This benchmark study of multinational organizations provides a clear understanding of the differences between compliance and non-compliance costs incurred when complying with laws, regulations and policies.
Main Resources:
- Main page of the report and material
- Videos
- Clarifying blogs
- An extract from blog 1:
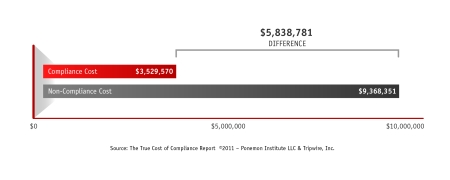
Succinctly put, compliance costs are proactive spending, while non-compliance costs are reactive spending. In this graph we can see that non-compliance costs are much more expensive than compliance costs — 2.65 times more expensive to be precise. However, this does not mean that an organization that spends on compliance will not experience non-compliance costs. What it tells us is that the total cost of compliance is very high because you’re balancing the preventative costs of compliance with the costs of failure, i.e. the reactive costs of non-compliance.
-
- Charts
- Audio podcast (33 min), (good one)
Findings
- the cost of non-compliance can be more expensive than investing in compliance activities
- industry and organizational size affect the cost of compliance and non-compliance
- the gap between compliance and non-compliance cost is related to number of records lost or stolen in data breaches
- the more effective an organization’s security strategy is, the lower the cost of non-compliance
- ongoing internal compliance audits reduce the total cost of compliance
- laws and regulations are the main drivers for investment in compliance activities