Forrester is publishing an interesting map “Privacy and Data Protection by Country” (Global heat Map), which provides a status overview in the world.
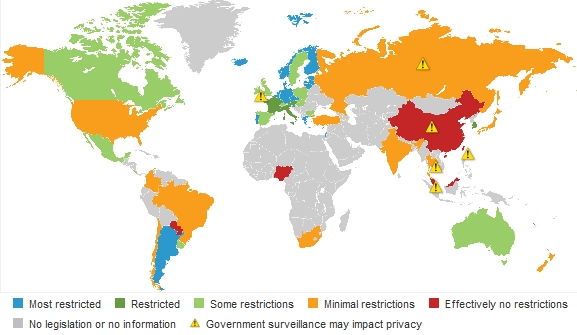
Forrester is publishing an interesting map “Privacy and Data Protection by Country” (Global heat Map), which provides a status overview in the world.

GSMA has prepared privacy guidelines within their “GSMA Mobile Privacy Initiative“.
What this is about?
See their brochure:
In January 2011, the GSMA published a set of universal Mobile Privacy Principles that describe the way in which mobile consumers’ privacy could be respected and protected when consumers use mobile applications and services that access, use or collect their personal information.
GSMA also published a discussion document in April 2011, outlining a set of Privacy Design Guidelines for Mobile Application Development.
Privacy Design Guidelines for Mobile Application Development
(Shortened list for readability)
NASA’s Curiosity robot has reached Mars surface.
Article with 10 min intro video “Target Mars: Rover Lands on the Red Planet“
Links
Note
Depending on findings (minerals, water, life?), the impact might be big!
Next
Disturbing news, see article “Mystery virus attack blows Qatari gas giant RasGas offline“.
It is worth to look article “IT’s 9 biggest security threats“
Questions: Where the world is going? What can individuals do? What can companies do?
GreatNews is a good alternative for reading news (RSS/Atom feeds)
Good:
The figure below shows the condensed view when using “Brief” style.
Automatic updates makes it possible to use this tool to display latest news on “newsboard”.
The figure below shows the handy search function applied to Feed Group Security.
OPML Example
The text below is created by exporting the BBC Feed Group from GreatNews tool.
Advanced
One can extend GreatNews functionality for a “newsboard” display by using a simple autoit script for automating the looping through all the feeds. See autoit script below; key F7 is send regularly into GreatNews tool.
While 1
WinActivate(“GreatNews”, “”)
WinWaitActive(“GreatNews”, “”, 30)
Send(“{F7}”)
Sleep(10000)
WEnd
With wine tool, one can run GreatNews (and autoit) also in linux environment.
Alternatives
Cybersecurity is clearly an issue for national security. 3 organizations have created a joined set of recommendations for governments.
Press release and Recommendations in June 2012.
The recommendations are:
Notes
This is good news for information security industry, ie. to address cybersecurity with a mature approach. It encourages to use standards and best practises. The issue is difficult. But also there are tools and methods to address this. The solution is not only to create one security unit for this, but to involve stakeholders, which we have many, in the process. Information security professionals are needed to guide and educate stakeholders into a mature approach.
Other links
The information is also available at EurActiv.