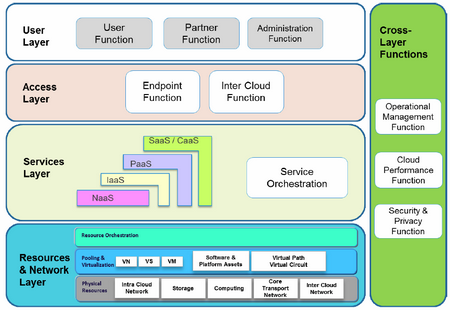
The work done by Focus Group Cloud (ITU-T) is now available as Technical Reports.
FG Cloud has been finished, and further work will take place in Study Groups…
This is interesting for anyone working in the area. The downloadable file contains 7 reports:
-
Part 1: Introduction to the cloud ecosystem: definitions, taxonomies, use cases and high-level requirements
-
Part 2: Functional requirements and reference architecture
-
Part 3: Requirements and framework architecture of cloud infrastructure
-
Part 4: Cloud Resource Management Gap Analysis
-
Part 5: Cloud security
-
Part 6: Overview of SDOs involved in cloud computing
-
Part 7: Cloud computing benefits from telecommunication and ICT perspective