In addition to your antivirus and firewall protection, one should consider Browser security.
In firefox , there are several settings related to security. At minimum, one should check security and privacy configurations.
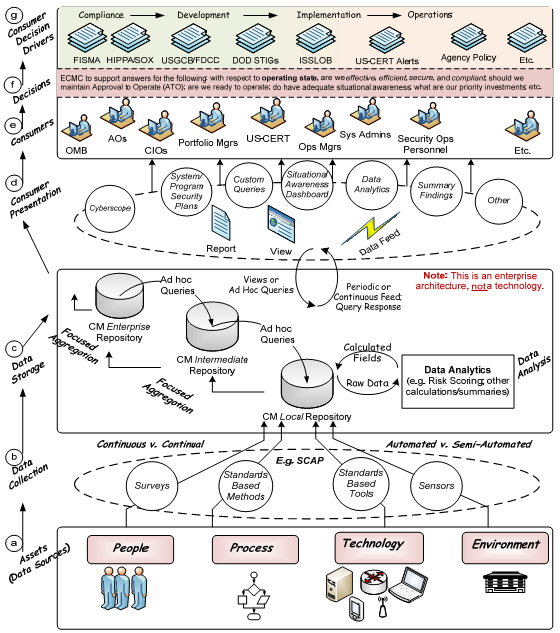
Security Settings
- Open Menu -> Tools -> Options, select “Security” panel
Recommendation: tick the first 3 settings
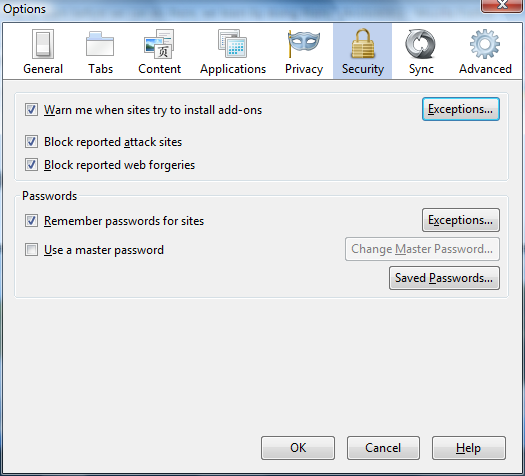
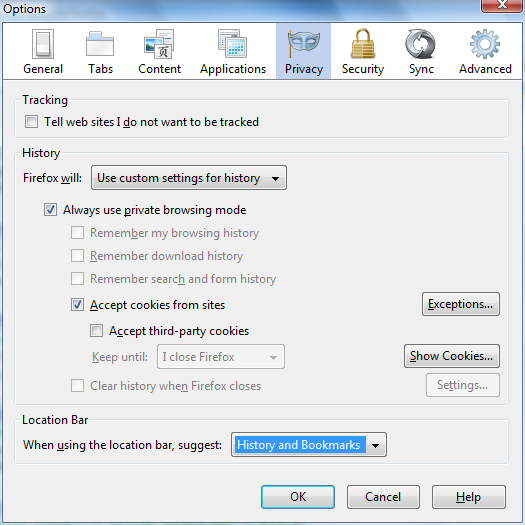
Privacy Settings
- Open Menu -> Tools -> Options, select “Privacy” panel
Recommendation:
- tick “Always use privacy browsing mode”
- tick “Accept cookies from sites”, but untick “Accept third-party cookies”
Alternative, one can use private browsing mode only occasionally via main menu.
- Menu -> Tools -> Start Private Browsing
- Menu -> Tools -> Stop Private Browsing
Review firefox settings
Review Add-ons list via main menu to see that only those add-ons which are needed are active.
See what is installed in “Extensions” and “Plugins”.
Security Add-ons
There are add-ons available for security and privacy. It is worth to look “BetterPrivacy” which protects agains long term cookies, and NoScript which prevents scripts from sites. NoScript need to be “trained”, since all scripts from all sites are disabled until explicitly configured otherwise.