BSIMM3 is model tool to compare your maturity against the industry average (earth), see figure below.
BSIMM = The Building Security In Maturity Model
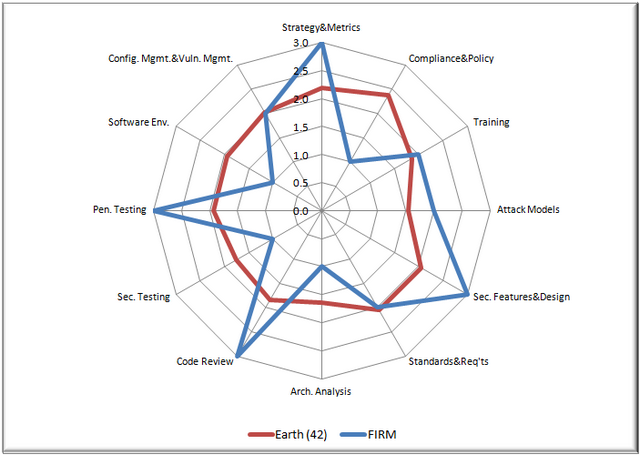
42 companies has particpated on this BSIMM project. Some of the company names are public: Adobe, Aon, Bank of America, Capital One, The Depository Trust & Clearing Corporation (DTCC), EMC, Fannie Mae, Fidelity, Google, Intel, Intuit, Mashery, McKesson, Microsoft, Nokia, QUALCOMM, Sallie Mae, SAP, Scripps Networks Interactive, Sony Ericsson, Standard Life, SWIFT, Symantec, Telecom Italia, Thomson Reuters, Visa, VMware, Wells Fargo, and Zynga.
The 42 companies represent industries as follows:
- financial services (17)
- independent software vendors (15)
- technology firms (10)
- telecommunications (3)
- insurance (2)
- energy (2)
- media (2)
- healthcare (1)
BSIMM3 describes 109 activities organized in 4 domains and 12 practices.
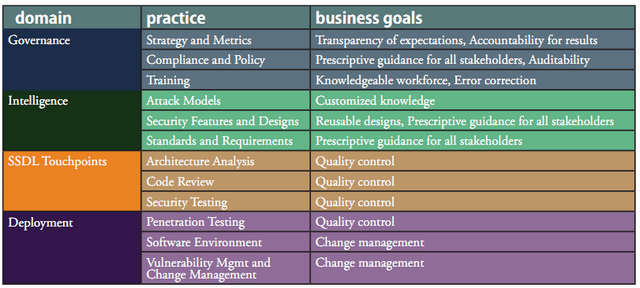
Term vBSIMM is used Vendor Control in the BSIMM. It includes five specific activities:
- Compliance & Policy activity 2.4: Paper all vendor contracts with SLAs compatible with policy.
- Compliance & Policy activity 3.2: Impose policy on vendors.
- Standards and Requirements acivity 2.1: Communicate standards to vendors.
- Standards and Requirements activity 2.5: Create SLA boilerplate.
- Training 3.2: Provide training for vendors or outsource workers.