Structured Threat Information eXpression STIX is a collaborative community-driven effort to define and develop a standardized language to represent structured cyber threat information.
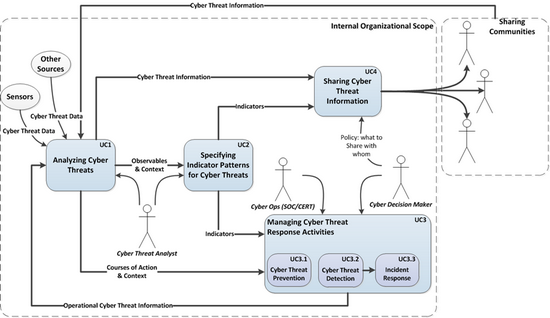
STIX Use Cases
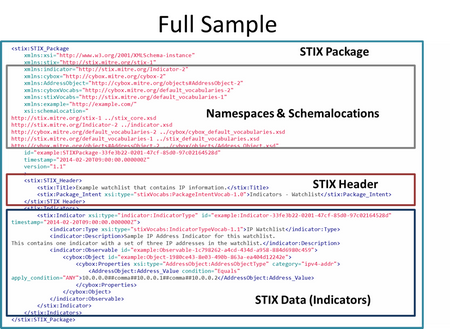
STIX sample
This is from the training material.
From samples page:
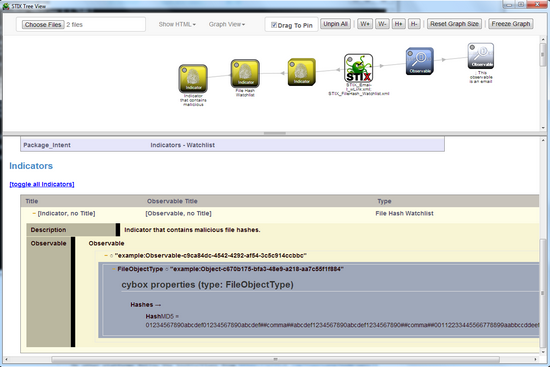
STIX Tree Viewer
One can use the tool STIX Tree Viewer from the training package.
See training material download on their training page.
StixViz.exe is included in the directory .\stix-taxii-workshop\stix\stix-viz
In the example below, 2 files were selected from the .\stix-taxii-workshop\stix\samples directory.
from FAQ
C2. What is the relationship between STIX and CybOX?
STIX uses the Cyber Observable eXpression (CybOX™) language to describe cyber Observables. The CybOX schema is natively imported and used within STIX to characterize system and network events, characteristics, and behaviors observed within the operational domain.
C5. What is the relationship between STIX and OpenIOC?
STIX Indicators can convey non-standard Indicator patterns in formats other than CybOX using the Test_Mechanism structure. Each format must be implemented as an extension of the Test_Mechanism extension point. STIX provides a default extension for Mandiant’s Open Indicators of Compromise (OpenIOC) as well as extensions for the Open Vulnerability and Assessment Language (OVAL®), SNORT rules, and YARA rules.
Other links
- CybOX Cyber Observable eXpression
- standardized schema for the specification, capture, characterization, and communication of events or stateful properties that are observable in the operational domain
- IOC Bucket
- shared IOCs
- TAXII Trusted Automated eXchange of Indicator Information (TAXII) is the main transport mechanism for cyber threat information represented as STIX
- blog “Indicators of Compromise, OpenIOC and CyBOX “
- Incident vs. Indicator