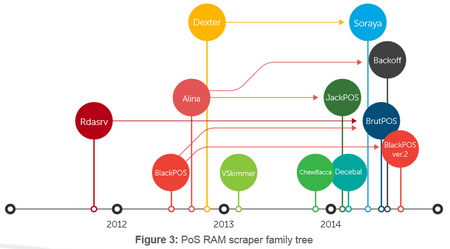
Increasing number of attacks has been taken against Point of Sales devices and systems. There are several good overviews and materials on this topic, and those are revealing details of the technics used in these targeted attacks.
Main sources
- PoS RAM Scraper Malware
- Combatting Point-of-Sale Malware
- Criminals follow their own software development lifecycle (SDLC) and test and retest their malware against anti-virus solutions to ensure it evades detection.
- Keyloggers, Memory Dumpers, Network Sniffers
- Criminals follow their own software development lifecycle (SDLC) and test and retest their malware against anti-virus solutions to ensure it evades detection.
- Demystifying Point of Sale Malware and Attacks
- Attacks on point-of-sales systems
- When a card is swiped, its details are briefly stored in the terminal’s memory while being transmitted to the payment processor. This provides a brief window for malware on the terminal to copy the card data, which it then transmits back to the attackers. The technique is known as “memory scraping” and it
is behind most of the major POS malware attacks seen in 2013 and 2014. - While EMV is commonly used in some parts of the world such as Europe, US merchants in particular have been slow to adopt the EMV standard and will not start implementing it until 2015.
- A look at Point of Sale RAM scraper malware and how it works
- Dexter and Project Hook Break the Bank
Other Links
- Point-of-Sale Malware Threats
- Backoff: New Point of Sale Malware
- Alert (TA14-002A) Malware Targeting Point of Sale Systems
- Backoff POS Malware Evolves
- The latest version of Backoff, dubbed “ROM,” includes upgrades that encrypt connections between infected – or zombie – systems, and attackers’ command-and-control servers
- ROM – A New Version of the Backoff PoS Malware
- Cardholder Information Security Program (CISP), Tools & FAQ
- Retail Merchants Targeted by Memory – Parsing Malware-UPDATE
Incidents