Vormetric has published a set of documents as part of the Vormetric 2015 Insider Threat Report. The research has been conducted by Harris Poll and analyzed by Ovum. Some short extracts are shown below. Worth to have a look.
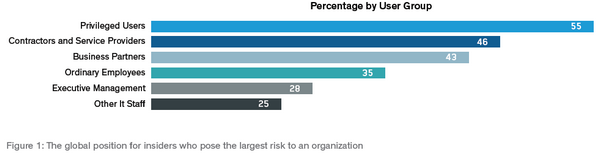
The most dangerous insiders have privileged access
For far too long systems administrators and business users with privileged access to the most sensitive corporate data have had open access, with few controls placed on their rights of entry. Even today only half of all business organizations have deployed privileged access/identity management (PAM or PIM) technology. But what has changed, and is clearly reflected in the Insider Threat Report survey results, is that senior management concerns over privileged user access have reached the top of their security agendas.
At the same time, insider access controls for other high-risk groups should not be ignored. The survey results suggest that other IT staff, many of whom have all the skills required to instigate an insider attack, are to a large extent being overlooked.
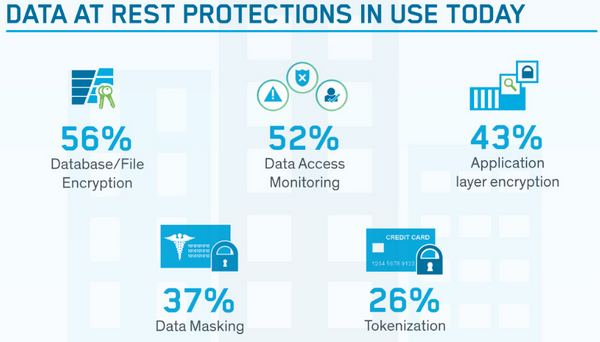
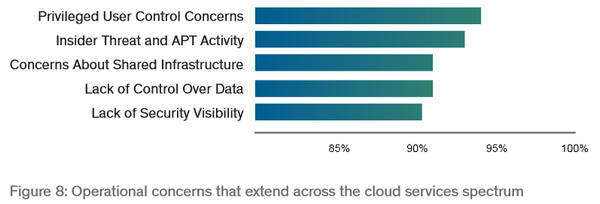
There also is other editions, like European Edition and Cloud and Big Data Edition. The figure below shows the main concerns for data within cloud environments.