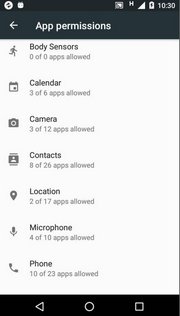
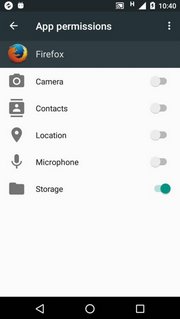
Android version 6, Marshmellow, has adopted a new run-time permission system that is available to the users. Permissions are divided into permission groups and users can modify permissions per application. It is possible to see how many applications are allowed in each group, and what permissions are applicable for each application. Please go to “Settings –> Apps” to find out.
Screenshots
“Permission groups” “Example: Firefox permissions” “3pp App showing more details”
Links for permission settings:
- How to Manage App Permissions on Android 6.0
- Android 6.0 Marshmallow, thoroughly reviewed: Permissions, Google Now on Tap
-
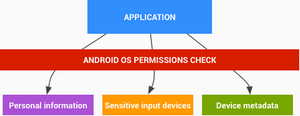
Android software stack
The following table is from developer pages “Permissions“:
Permission Group Permissions CALENDARREAD_CALENDAR
WRITE_CALENDARCAMERACAMERACONTACTSREAD_CONTACTS
WRITE_CONTACTS
GET_ACCOUNTSLOCATIONACCESS_FINE_LOCATION
ACCESS_COARSE_LOCATIONMICROPHONERECORD_AUDIOPHONEREAD_PHONE_STATE
CALL_PHONE
READ_CALL_LOG
WRITE_CALL_LOG
ADD_VOICEMAIL
USE_SIP
PROCESS_OUTGOING_CALLSSENSORSBODY_SENSORSSMSSEND_SMS
RECEIVE_SMS
READ_SMS
RECEIVE_WAP_PUSH
RECEIVE_MMSSTORAGEREAD_EXTERNAL_STORAGE
WRITE_EXTERNAL_STORAGE
More details from “Application security: Permission model“:
- These resources are only accessible through the operating system.
- The user can not grant or deny individual permissions — the user must grant or deny all of the requested permissions as a block.
- applications that are included in the core operating system or bundled by an OEM do not request permissions from the user
More details from developer docs:
Normal permissions cover areas where your app needs to access data or resources outside the app’s sandbox, but where there’s very little risk to the user’s privacy or the operation of other apps.
Dangerous permissions cover areas where the app wants data or resources that involve the user’s private information, or could potentially affect the user’s stored data or the operation of other apps
For a list of normal permissions, see here. For a full list of permissions, please see Manifest.permission.
Permission element, PermissionInfo, protectionLevel
When looking the developers docs, the real story is more complex. For example, there is a full list of protection levels defined as
- normal
- dangerous
- signature
- signatureOrSystem
- privileged
- system
- development
- appop
- pre23
- installer
- verifier
- preinstalled
Other related
- Assist application has many permissions, but can be turned off. (See Apps–>Default Apps–>”Assist & voice input”)
- “Ok Google” voice recognition can be turned off. (Deny access to microphone).
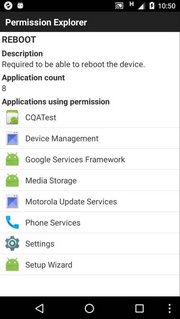
- Permission Explorer is quite handy to browse through permissions.
Summary
It is great that there are more controls for the user. This is significant improvement for many users. In addition, there are several related configurations spread around the settings tool, and one would need to go through all possible settings. For example, one have to select “Show system” option inside “Microphone permissions” under “App Permissions” to see also the system applications, and not only the ones that you have installed yourself…
If privacy is your concern, then this improvement does not guarantee that you would have full control.
Additional “on device” alternative for the privacy
There are some additional steps that one can do.
- Use only local calendar. (Can be created by MyPhoneExplorer)
- Use only local account for Contacts. (Can be created by MyLocalAccount)
- Use local firewall to block unwanted traffic. (Can be done with NoRoot Firewall, creates a local VPN to filter traffic)
- Turn off GPS, and/or data traffic when not needed
Please note that email clients/solution have not been included here. Those should be evaluated case by case.