Introduction
OpenWrt is a Linux distribution that can be loaded into many wireless routers by replacing the original firmware with OpenWrt firmware. The picture below shows 2 such routers, together with Raspberry Pi on the right for comparison.

My interest on Openwrt was to figure out if it can be used to provide better protection at home network. I also wanted to see that what traffic there really is, and how I can better control it.
Some history: I was not positively surprised when I realized that the USB device that I was using was automatically checking and downloading software update. I thought that installing the USB driver the first time was sufficient, since this USB device had nothing to do with networking. But no, without informing about it, it simply had been doing the automatic downloads until I happened to find it out.
From wikipedia:
The project came into being because Linksys built the firmware for their WRT54G series of wireless routers from publicly available code licensed under the GPL. Using this code as a base and later as a reference, developers created a Linux distribution that offers many features not previously found in consumer-level routers. The code names of OpenWrt branches are named after alcoholic beverages…
Openwrt software packages
These routers do not have much computing power but often by using Openwrt one can get more functionalities than by using the original firmware. There are several packages available in the download area. But if one installs anything that is too heavy then there will be a downgrade on network performance.
Some potentially useful features:
- filtering web proxy (Privoxy, tinyproxy)
-
- also transparent proxy setup
- firewall
- online USB storage
- wireless access for guests (guest WLAN)
- captive portal
- bandwith monitoring
- port mirroring
- network troubleshooting
- dynamic DNS
- openVPN
- port knocking
- IPset administration utility
One might be able to operate and configure the router mostly via web. But the truth is that command line interface is often needed for detailed configurations and troubleshooting. For example, the original firmware would support the USB storages, but with Openwrt some operations on command line are needed in order to configure the USB storage devices. Needless to say that even though there is documentation, it is still difficult to find good instructions that work for you. This is due to so many different Openwrt software releases and hardware devices.
Summary of 2 different wireless routers
I have tested some Openwrt features on 2 different routers that supports Openwrt: Buffalo WHR-HP-300N and TP-link TL-WR1043ND . For other devices that support Openwrt, please see the list. The table below summarizes the result when focussing on controlling the network traffic better with firewall and with web proxy.
| Software | WHR-HP-300N | TL-WR1043ND
(see recommended routers) |
|---|---|---|
| Firewall | configured via web GUI | configured via web GUI |
| web proxy (tinyproxy) | installed via command line, configured via web GUI. | installed via command line, configured via web GUI. This proxy works for both http and https. (However, for https it does not show any good error page for rejected sites.) |
| USB storage | no USB | following the instructions, USB storage is working. On client side one can use WinSCP with SCP protocol to access any file in router. |
| Network monitoring | port mirroring was possible via iptables. In this scenario, the traffic to certain IP address was copied into another IP address, and it does not depend on which physical ports of the switch are used. There was no space to install tcpdump, |
port mirroring between physical ports was easily possible since it is supported by internal switch. (See below about the chapter on port mirroring) iftop, command line tool, is working fine. |
| command line (ssh) | activated & configured via GUI, need to add port forwarding if want to access it from wan side. |
activated & configured via GUI, need to add port forwarding if want to access it from wan side. |
| Openwrt installation Chaos Calmer 15.05 |
via original web GUI | via original web GUI |
| Flash memory | 4M | 8M |
| RAM memory | 32M | 64M |
| CPU | Atheros AR7240
Target: ar71xx |
Atheros QCA9558
Target: ar71xx |
| internal switch | Atheros AR7240 | Atheros AR8327N Note: outside LAN port 1 = internal switch port 4 outside LAN port 2 = internal switch port 3 outside LAN port 3 = internal switch port 2 outside LAN port 4 = internal switch port 1 |
| NW speed (MHz) | 10/100 | 10/100/1000 |
| WiFi chip | Atheros AR9283 | Atheros QCA9558 |
TL-WR1043ND with firewall and web proxy
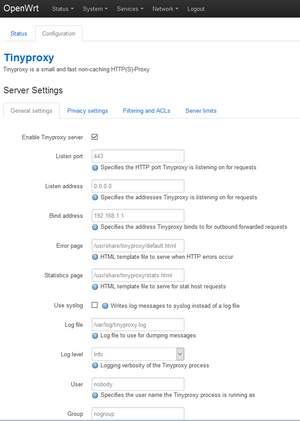
Before restricting the traffic with firewall, it is better to configure the proxy “tinyproxy” and test that it is working. It is assumed that transparent proxy is not used, but proxy need to be configured manually at each client.
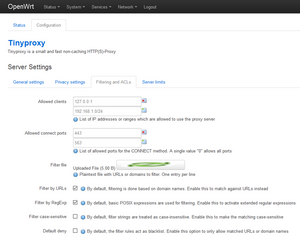
The picture on the left below shows the configuration settings. These GUI menus were available after installation of tinyproxy, as there is specific GUI app for it. In this current setup, port 80 is used for the openwrt GUI and port 443 is used for the tinyproxy at the router. (The listen address could also be “192.168.1.1”, but then the tinyproxy statistics GUI did not work). The picture on the right shows the settings for the filtering. The file with filtering conditions, can be updated via GUI.
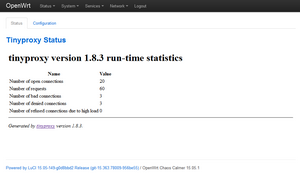
The picture below shows the status window.
The URL traffic log is available at file “/var/log/tinyproxy.log”. The “not allowed” traffic is visible in a line as ‘Proxying refused on filtered url “yyy”‘. For http the full URL is visible; for https only the protocol, hostname and port are visible, but not the path or file name.
After web proxy was working, then next was the firewall configuration. Again this is possible and easier to do via web GUI. One can use command line to see the configuration “cat /etc/config/firewall”.
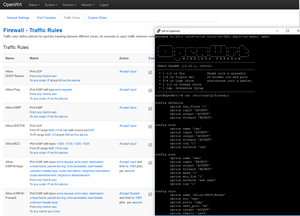
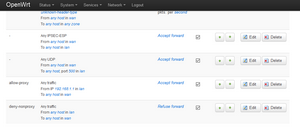
The picture below shows the new firewall rules to deny traffic from lan to wan (rule “deny-nonproxy”), except from the web proxy (rule “allow-proxy”).
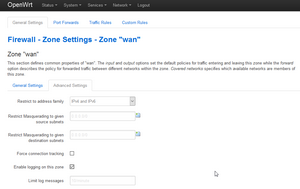
The next picture shows “Firewall Zone settings: Enable logging on this zone”. This is needed in order to see what traffic does not go through the firewall. One can see the rejected traffic in the menu Status->System Log (or using “logread” via the command line).
For existing connections, one can look at Status-> Realtime Graphs->Connections.
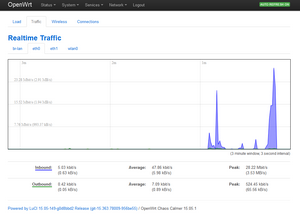
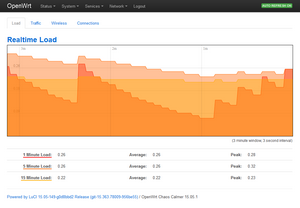
Other: The 2 figures below show the other real time graphics: traffic and load.
Other: Planning to test TL-WR1043ND with ipset
Big blacklists can effect the performance. Managing of firewall blacklists could be easier with ipset (IPset administration utility). There are several source for blacklist. for example here, here, here and here. (There is also a list of IP addresses by country.)
Other: TL-WR1043ND with port mirroring
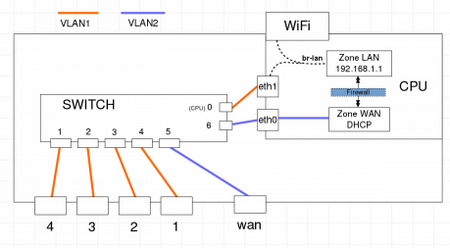
The instructions at the openwrt site are showing configuration settings for port mirroring. This switch supports the port mirroring, and therefore there is no need to do this via iptables. However, it is possible to do this configuration also via web GUI. Please note that the internal switch port number and the outside LAN connectors are not the same. The figure below shows the networking setup of this wireless router. In order to see (and capture) the traffic in the monitor port, remember to put the network interface into prosmicious mode when using a tool like wireshark.
The picture below shows the port mirroring configuration in the web GUI, and the corresponding printout via command line “cat /etc/config/network”. The traffic in the physical port 4 (LAN port 4) was copied into physical port 1, where a PC with wireshark was running.
Other: opkg package manager
Installations can easily be done via command line, thanks to opkg. If the space is runned out while installation, then one need to clean up manually. Here below are some opkg commands to show details about iftop package. Since the actual firmware area is read-only, the actual location of the file is in /overlay…
root@OpenWrt:~# opkg info iftop Package: iftop Version: 1.0pre2-1 Depends: libc, libpcap, libncurses, libpthread Status: install user installed Architecture: ar71xx Installed-Time: 1483024587 root@OpenWrt:~# opkg status iftop Package: iftopVersion: 1.0pre2-1 Depends: libc, libpcap, libncurses, libpthread Status: install user installed Architecture: ar71xx Installed-Time: 1483024587 root@OpenWrt:~# opkg files iftop Package iftop (1.0pre2-1) is installed on root and has the following files: /usr/bin/iftop root@OpenWrt:~# ls -la /usr/bin/iftop -rwxr-xr-x 1 root root 33640 Jan 31 2016 /usr/bin/iftop root@OpenWrt:~# ls -la /overlay/upper/usr/bin/iftop -rwxr-xr-x 1 root root 33640 Jan 31 2016 /overlay/upper/usr/bin/iftop
Other: additional statistics
One can get more statistics on openwrt GUI with additional packages, see Statistical Data Overview and luci-app-statistics.
It is possible to send all the different logs via syslog or syslog-ng into another host for even better analysis…
WHR-HP-300N
This router has much less space for installing additional packages.
root@OpenWrt:~# cat /proc/cpuinfo system type : Atheros AR7240 rev 2 machine : Buffalo WHR-HP-G300N processor : 0 cpu model : MIPS 24Kc V7.4 BogoMIPS : 265.42 wait instruction : yes microsecond timers : yes tlb_entries : 16 extra interrupt vector : yes hardware watchpoint : yes, count: 4, address/irw mask: [0x0ffc, 0x0ffc, 0x0ffb, 0x0ffb] isa : mips1 mips2 mips32r1 mips32r2 ASEs implemented : mips16 shadow register sets : 1 kscratch registers : 0 package : 0 core : 0 VCED exceptions : not available VCEI exceptions : not available root@OpenWrt:~# df -h Filesystem Size Used Available Use% Mounted on rootfs 448.0K 252.0K 196.0K 56% / /dev/root 2.3M 2.3M 0 100% /rom tmpfs 14.0M 492.0K 13.6M 3% /tmp /dev/mtdblock5 448.0K 252.0K 196.0K 56% /overlay overlayfs:/overlay 448.0K 252.0K 196.0K 56% / tmpfs 512.0K 0 512.0K 0% /dev
VPNs and WRT
Both OpenWrt and DD-Wrt other usefull security related features. For a VPN related comparison, one could look comparison of VPNs on DD-Wrt.