With open source EIDAuthenticate it is possible to use 2-factor authentication, smart card + PIN, to login to Windows. EIDAuthenticate is for Windows Vista & later on stand alone computer (computer not in domain, ie. no Active Directory in use).
What is needed
-
Software EIDAuthenticate
-
Smart Card Reader
-
I used akasa élite
-
-
Smart Card
-
I used MyEID PKI Card
-
-
A local user account
List of supported cards can be found on their web site. A more complete list with details, is also available.
Flow
-
Install first card vendor’s tools and drivers (ActiveSecurity MyClient), and then EIDAuthenticate.
-
Initialize the card. I used initialization script “small” which basically creates 3 PINs on the card: Basic, Signature and Management (SO). At this point, there is no certificates on the card yet.
-
Follow instructions, start by launching the wizard in the Windows Control Panel.
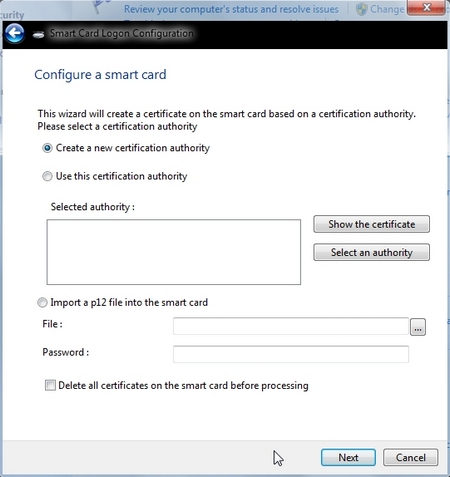
- At the end of the wizard, there is a test to verify if PIN works. After succesfull test, wizard ask if result can be send to online database.
Tips
-
Initialize the smart card with the card vendor’s tools (not with opensc).
-
The self signed Root certificate created by the wizard is visible in the Certificate Manager tool (certmgr.msc) in Windows 7. Look the certificates under tree branch “Trusted Root Certification Authorities\Certificates”.
-
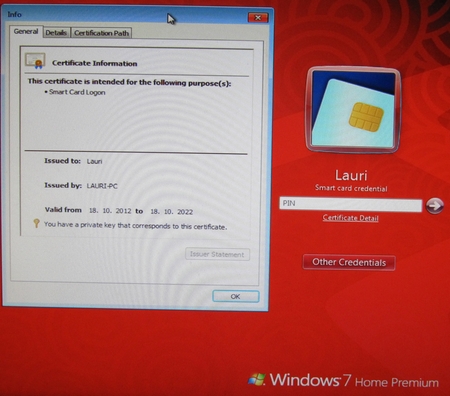
Before logon attempt, one can view certification path via link “Certicate Details” (see first figure in this blog).
-
For troubleshooting, one can use EIDLogManagertool.
-
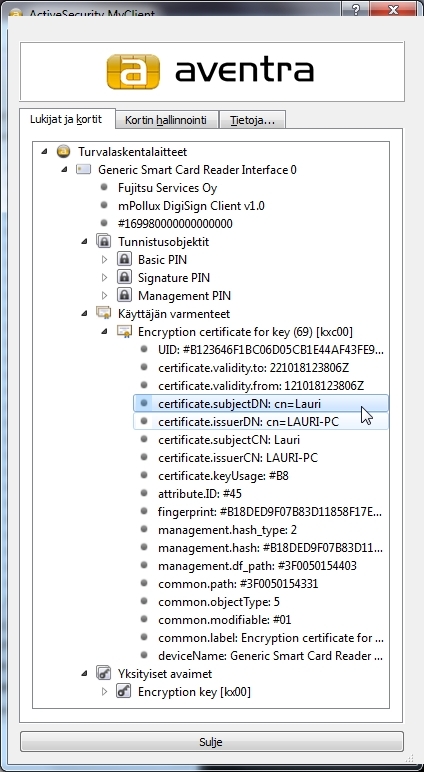
One can use card vendor’s tool, or opensc, to view the content of the smart card. The figure below shows the card vendor’s tool. The certificate on the card is for user “Lauri”, issued by “Lauri-PC”.
pkcs15-tool –read-certificate 45 –output certificate.pem
- and to extract issuer and subject out from the certificate, can be done by commad
openssl x509 -in certificate.pem -issuer -subject -noout
- which is the same as subjectCN and issuerCN in figure above.