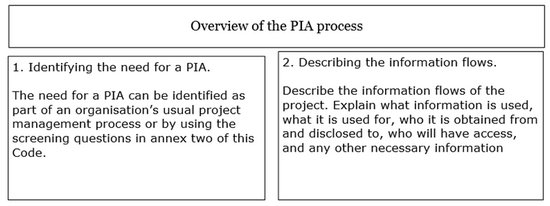
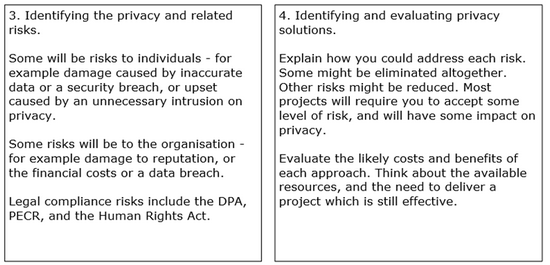
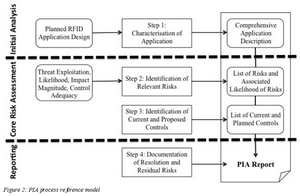
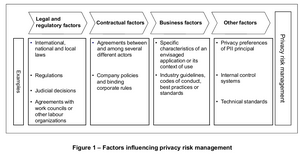
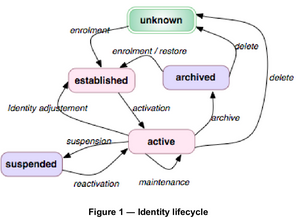
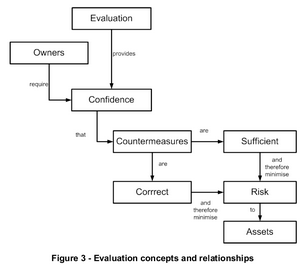
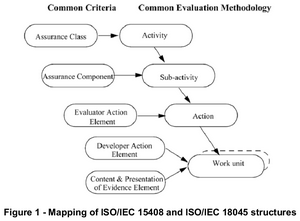
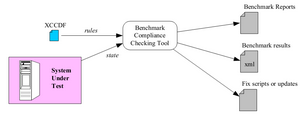
The following “Internet evolution” drawing has been on the different slides in ETSI workshops. It can be found in slide 4 in the M2M architecture overview presentation.
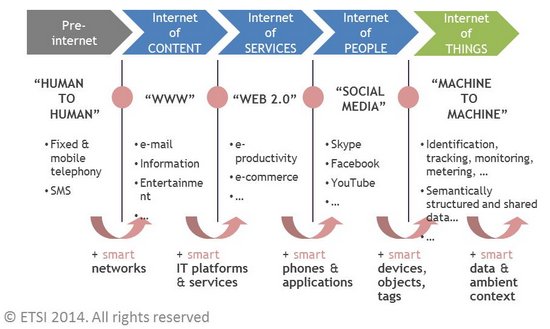
It nicely compares “Internet of content”, “Internet of services”, “Internet of people” and “Internet of things”.