I have a 12MP, 12x optical zoom digital camera, Canon PowerShot SX200, and I wanted to see how well that fits to shooting constellations and stars. This camera has manual settings as well. (camera review)
I was going after the Jupiter. With Stellarium, one can easily find Jupiter’s location at any given hour.
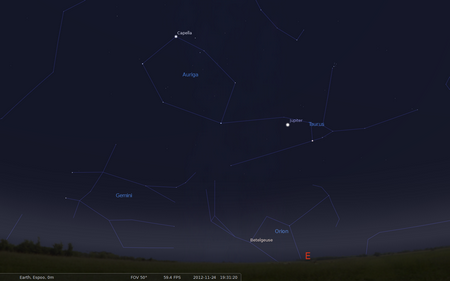
It had been cloudy for many days, but luckily at least some sky became visible last night. The photo below is without any zoom applied, showing wheather conditions (cloudy and with light pollution). Stellarium is used to identify the stars and constellations.
The photo details (EXIF info from Irfanview tool)
-
ShutterSpeedValue – 2 seconds
-
ApertureValue – F 3.40
-
FocalLength – 5.00 mm
-
ISO Value – 1600
The next photo of Jupiter is taken with maximum zoom. For better results, the camera settings would need to be optimized. However even with these first photos, even some weak stars leave their marks on the photos 🙂
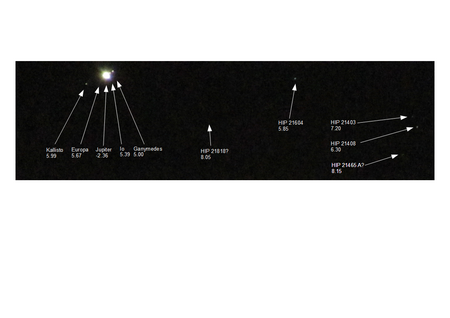
The photo details
-
ShutterSpeedValue – 2 seconds
-
ApertureValue – F 5.30
-
FocalLength – 60.00 mm
-
ISO Value – 1600
The next photo of Moon is also taken with maximum zoom (one day later). Not bad for a compact camera.

The photo details
-
ShutterSpeedValue – 1/403 seconds
-
ApertureValue – F 5.30
-
FocalLength – 60.00 mm
-
ISO Value – 80
Results
Taking into consideration the wheather conditions and that camera settings were not optimized, I’m quite satisfied with results. Definitely it is worth to try to get better pictures later.
Tips
- There are several “night sky” tools available for android phones making it easier to find the planets and stars.
- To minimize vibrations, it was better to use 10sec timer instead of 2 sec.
How about Cameras with 24-zoom
I found this page, where the quality of the photos are much better than I could get (and would get). See the Jupiter and Moon photos here. Those photos are taken with Panasonic Lumix FZ150.
And how about Telescopes?
I do have an entry level telescope Meade ETX70AT (link to info)

And using the same camera attached to ETX70, I got a photo of the moon. (Again, a lot of adjustments could be improved. In any case this photo has much more pixels than the moon photo above.)
However, for “real” photos, a better telescope is needed (one of my dreams). Then one can take photos like these in the LX200 gallery
And perhaps you might find surprises! For example see page “Explosion on Jupiter Spotted by Amateur Astronomers” which was taken with LX200GPS. The video is great.