EssentialPIM is a good alternative for Personal Information Manager tool.
Good:
- Combined set of tools:
- appointments, tasks, notes, contacts, password entries and email messages
- password protected tool
- possible to import contacts etc.
- possible to synchronize with android via own application
Bad:
- Slow’ish operation sometimes (database)
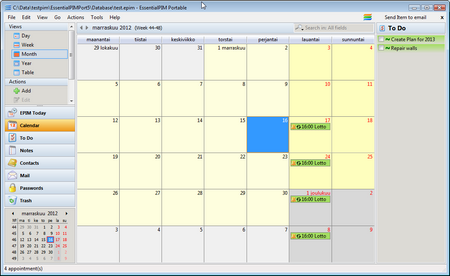
The figure below shows Calendar view. In the free edition, repetitive tasks (todo) are not enabled, but one can use calendar for the same purpose. In this case a reminder for the “Lotto”.
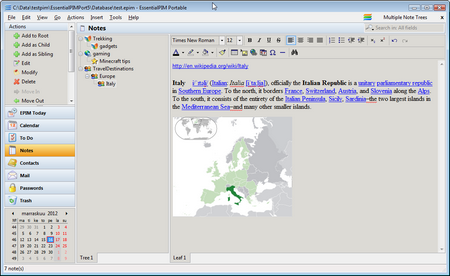
The above mentioned tools are available even in the free edition. By surpise, it seems that tree structure is supported in the Notes. In the figure below some text and figure is copied from wikipedia.
Tips
With free edition one cannot synchronize with outlook (pro version is needed). There are 2 alternatives to transfer Contacts from Outlook into EssentialPIM
- Alternative 1:
- Export contacts in outlook as individual vcf files, in Actions menu: Forward as vCard
- Import, in EssentialPIM, use File:Import:Contacts:vCard
- Alternative 2:
- Export contacts and other data in outlook inside pst file
- File->New->Outlook Data File
- for example test.pst
- Select this pst file inside Outlook, and Create new folder with type Contact
- for example name “PersonalContacts”
- Select “Contacts” menu in Outlook, and now the “PersonalContacts in test” is visbile under “My Contacts”
- Copy your contacts into this new contact list (“PersonalContacts”)
- Close test.pst
- File->New->Outlook Data File
- Import, in EssentialPIM, use File:Import:Outlook
- Export contacts and other data in outlook inside pst file
Note!
I have categorized this in the Advanced Tools, because at the same time as it can facilitate the tasks, at the same time it can be more risky, if backups are not taken regularly. And care is need in order not to blowup the tool with information. For example, for notes one could use another instance, or another tool like keynote NF. And for passwords, one could use Keepass. But all in all, use with care since a lot of information in one place…