In addition to Lingoes, GoldenDict is another free tool for dictionaries and thesauruses. The tools are very similar. For example, GoldenDict can be used both online and offline dictionaries.
The difference is that one can use GoldenDict to open your own dictionaries in *.bgl format or in *.dsl format. Lingoes does not have any good support for importing your own dictionaries. There is no “easy and straightforward” way to create your own dictionaries by using these free tools. While using free method, it is possible to create glossaries etc. but for more serious thesaurus with better look and feel, commercial tools are better choise.
BGL format
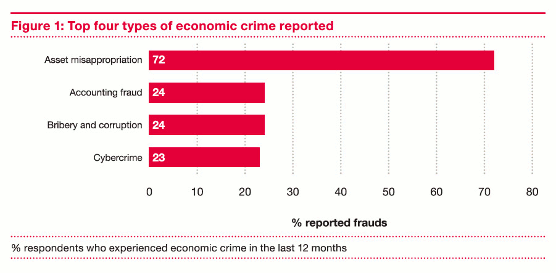
BGL format is used by a commercial Babylon tool. Babylon Builder is free tool for creating dictionary (licenced for private user only). The support is mainly for excel files, as explained here. The figure below shows an excel containing definitions, and Builder GUI for processing the excel columns. However, I found this way very limited. This could be usefull method if you have definitions in column format, and you are not aiming to include figures.
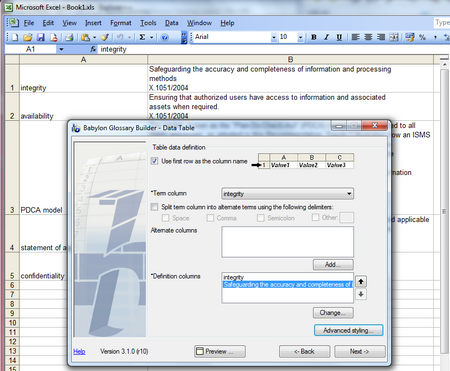
Luckily, an old tool Babylon Builder 1.0.63 is presented in GoldenDict’s Forum pages (including download link). This tool provides simple GUI for creating dictionary without “programming” (see figure below). It supports very limited html; links and figures. The output of this is visible in the first figure (above).
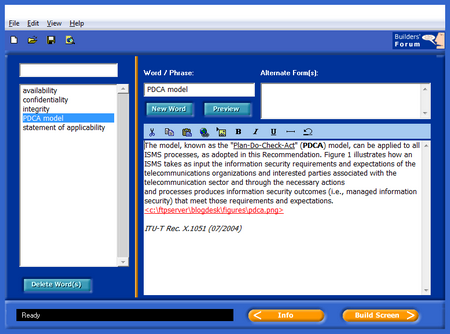
GLS format
GLS file format is an alternative, where the raw data is in simple text format. GLS file needs to be converted into binary BGL format so that GoldenDict can read it. Convertion can be done with new or old version of the Babylon Builder tool (see above). The format of the file is described in babylon page.
[blank line]
Term | Alternate1 | Alternate2| … | AlternateK
[attributes]
Definition
[blank line]
An example is here below:
### Glossary title:ITU-T Security Dictionary Test
### Author:Lauri Säisä
### Description:Security related terms and definitions used in ITU-T recommendations.
### Source language:English
### Source alphabet:Default
### Target language:English
### Target alphabet:Default
### Icon:
### Browsing enabled?Yes
### Type of glossary:00000000
### Case sensitive words?0
### Glossary section:
availability
Ensuring that authorized users have access to information and associated<BR>assets when required.<BR>X.1051/2004
confidentiality
Ensuring that information is accessible only to those authorized to have<BR>access.<BR>X.1051/2004
integrity
Safeguarding the accuracy and completeness of information and processing<BR>methods<BR>X.1051/2004
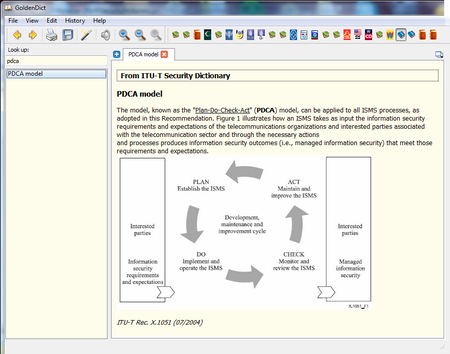
PDCA model
The model, known as the "<U>Plan-Do-Check-Act</U>" (<B>PDCA</B>) model, can be applied to all ISMS processes, as adopted in this Recommendation. Figure 1 illustrates how an ISMS takes as input the information security requirements and expectations of the telecommunications organizations and interested parties associated with the telecommunication sector and through the necessary actions<BR>and processes produces information security outcomes (i.e., managed information security) that meet those requirements and expectations.<BR><img src=”c:\ftpserver\blogdesk\figures\pdca.png” align=”center”><BR><BR><I>ITU-T Rec. X.1051 (07/2004)</I>
statement of applicability
Document describing the control objectives and controls that are relevant and applicable to the organization’s ISMS, based on the results and conclusions of the risk assessment and risk treatment processes.<BR>X.1051/2004
DSL format as alternative
GoldenDict can read *.dsl files (used by ABBYY Lingvo tool), this could be used as an alternative format. In fact, this is easier format to maintain since GoldenDict can read this text format directly. Tips on how to create dsl files are available in GoldenDict forum pages (more). A sample dsl file (plain text) is available here.
There also exist a perl script TXT2DSL (direct link) to quickly convert simple data format file into dsl format. The tool expect each line to be in following format (tabulator is used to separate fields).
word <tab> translation <tab> explanation <tab> comment
The following example shows how dsl file looks like.
#NAME "My English Dictionary"
#INDEX_LANGUAGE "English"
#CONTENTS_LANGUAGE "English"
aba{·}cus
/ [s]abacusBr.wav[/s] 'æb?k?s; [p]NAmE[/p] [s]abacusUS.wav[/s] / [c]noun[/c] [s]abacus.jpg[/s]
([p]pl.[/p] [c darkcyan][b]aba·cuses[/b][/c] / [s]abacusesBR.wav[/s] -k?s?z; [p]NAmE[/p] [s]abacusesUS.wav[/s] /) a frame with small balls which slide along wires. It is used as a tool or toy for counting.
acquiesce
\[[t]æ_kwie_s[/t]\]
[m1][b][c]acquiesces[/b][i],[/i] [b]acquiescing[/b][i],[/i] [b]acquiesced[/b][/m]
[m1][p][i]VERB[/c][/i][/p][/m]
[m1][trn]If you [b]acquiesce[/b] in something, you agree to do what someone wants or to accept what they do. \[FORMAL\][/trn][/m]
[m2][*][ex][lang id=1033]\[[i][c]V in/to [p]n[/c][/i][/p]\] Steve seemed to acquiesce in the decision…[/lang][/ex][/*][/m]
[m2][*][ex][lang id=1033]\[[i][c]V in/to [p]n[/c][/i][/p]\] He has gradually acquiesced to the demands of the opposition…[/lang][/ex][/*][/m]
[m2][*][ex][lang id=1033]When her mother suggested that she should not go far from the hotel, Alice willingly acquiesced.[/lang][/ex][/*][/m]
[m1][*][b]Syn:[/b][/*][/m]
[m1][*][com]give in[/com], [com]submit[/com][/*][/m]
[m1][*][b]Ant:[/b][/*][/m]
[m1][*][ref]resist[/ref][/*][/m]
acquiesced
[m1]If you [b]acquiesce[/b] in something, you agree to do what someone wants or to accept what they do. \[FORMAL\][/m]
[m2][ex][c darkgray]\[[i][c]V in/to [p]n[/c][/i][/p]\] Steve seemed to acquiesce in the decision…[/c][/ex][/m]
[m1][com][c]give in[/c][/com][/m]
embed
\[[t]?mbe_d[/t]\]
[m1][b][c]embeds[/b][i],[/i] [b]embedding[/b][i],[/i] [b]embedded[/c][/b][/m]
[m1]1) [p][i][trn]VERB[/i][/p] If an object [b]embeds[/b] itself in a substance or thing, it becomes fixed there firmly and deeply.[/trn][/m]
[m2][*][ex][lang id=1033]\[[i][c]V [p]n[/p] in [p]n[/c][/i][/p]\] One of the bullets passed through Andrea’s chest before embedding itself in a wall [url]http://www.google.com[/url].. \[[i][c]Also V [p]n[/p] [p]prep[/c][/i][/p]\][/lang][/ex][/*][/m]
[m2][*][b]Derived words:[/b][/*][/m]
[m2][*][b][lang id=1033]embedded[/b] [i][c]ADJ-GRADED[/c][/i] [i][c]oft ADJ in [p]n[/c][/i][/p] [ex]The fossils at Dinosaur Cove are embedded in hard sandstones…[/ex] [ex]There is glass embedded in the cut.[/lang][/ex][/*][/m]
[m1]2) [p][i][c][trn]VERB:[/p] usu [p]passive[/c][/i][/p] If something such as an attitude or feeling [b]is embedded[/b] in a society or system, or in someone’s personality, it becomes a permanent and noticeable feature of it.[/trn][/m]
[m2][*][ex][lang id=1033]\[[i][c]be [p]V-ed[/p] in [p]n[/c][/i][/p]\] This agreement will be embedded in a state treaty to be signed soon by Bonn and East Berlin.[/lang][/ex][/*][/m]
[m2][*][b]Derived words:[/b][/*][/m]
[m2][*][b][lang id=1033]embedded[/b] [i][c]ADJ-GRADED[/c][/i] [i][c]oft ADJ in [p]n[/c][/i][/p] [ex]I think that hatred of the other is deeply embedded in our society.[/lang][/ex][/*][/m]
Commercial Tools for custom dictionaries
ABBYY Lingvo is one alternative, which also supports custom dictionaries.
GoldenDict for Android
Please note, that there exist GoldenDict Free application for android.

 …
…