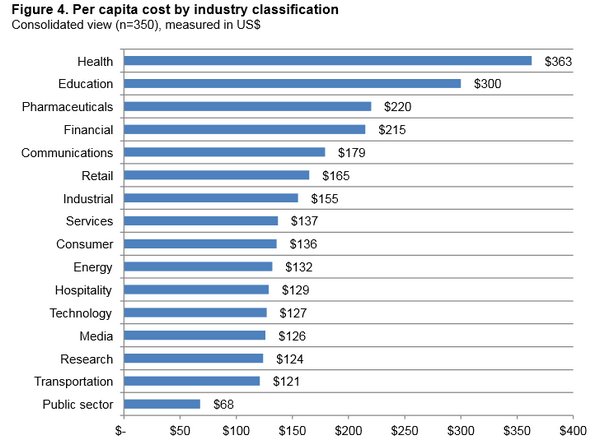
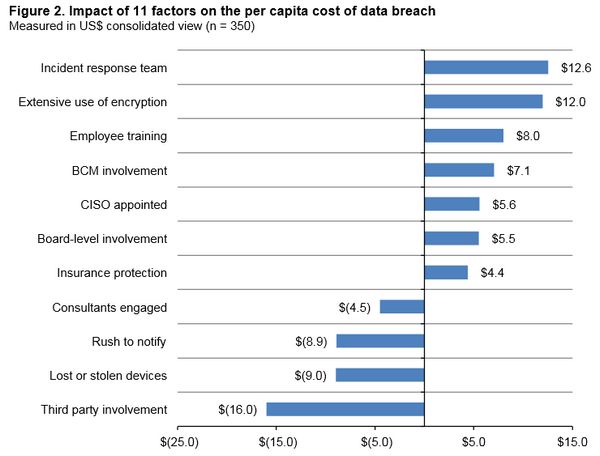
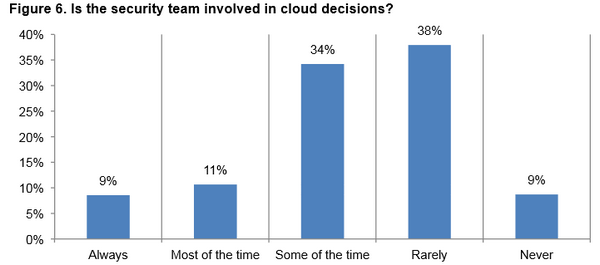
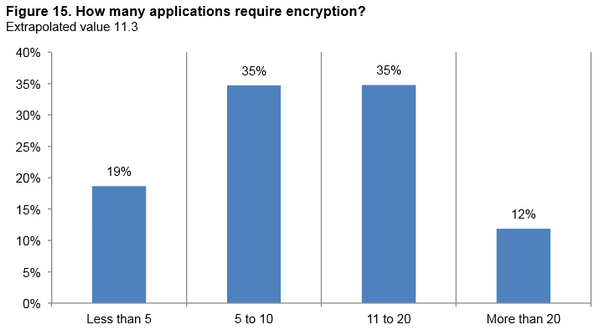
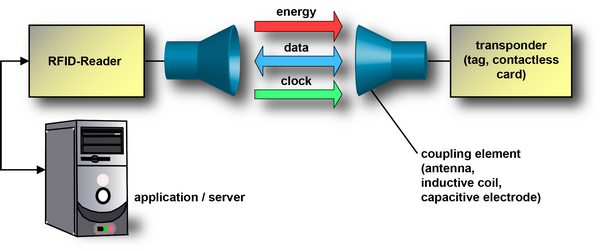
An RFID system is always made up of two components:
-
the transponder, Proximity Integrated Circuit Card (PICC)
-
the detector or reader , Proximity Coupling Device (PCD)
The RFID reader/writer (13.56MHz) RF522 for arduino can be used in Raspberry. In this first test, the steps described here and here were followed. They both are using the python source code. Please see these references for the correct connections between raspberry and the RC522 (see picture below).

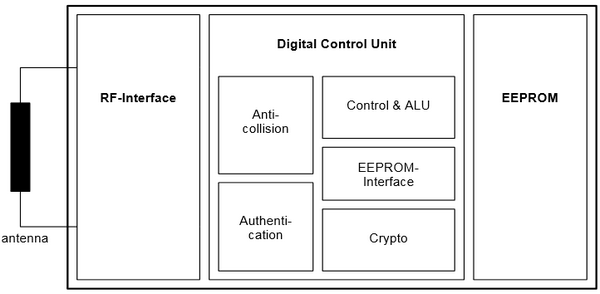
The reader can read MIFARE cards. The block diagram is shown below. The data in the EEPROM can be “read & write” with this RC522.
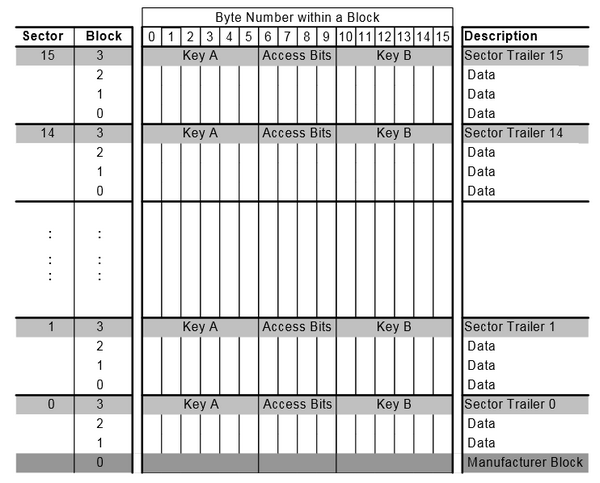
The 1024 x 8 bit EEPROM memory is organized in 16 sectors with 4 blocks of 16 bytes each.
In the test, the source code worked out from the box without any changes..
A small modifications were made on the code to change the printout.
Reading a card:
pi@raspberrypi ~/SPI-Py/MFRC522-python $ sudo python Read2.py
/home/pi/SPI-Py/MFRC522-python/MFRC522.py:113: RuntimeWarning: This channel is already in use, continuing anyway. Use GPIO.setwarnings(False) to disable warnings.
GPIO.setup(22, GPIO.OUT)
Welcome to the MFRC522 data read example
Press Ctrl-C to stop.
Card detected
Card read UID: 77,84,46,59
Size: 8
Sector 0 [77, 84, 46, 59, 12, 8, 4, 0, 98, 99, 100, 101, 102, 103, 104, 105]
Sector 1 [0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0]
Sector 3 [0, 0, 0, 0, 0, 0, 255, 7, 128, 105, 255, 255, 255, 255, 255, 255]
Dumping the content of 1K card:
pi@raspberrypi ~/SPI-Py/MFRC522-python $ sudo python Dump2.py
/home/pi/SPI-Py/MFRC522-python/MFRC522.py:113: RuntimeWarning: This channel is already in use, continuing anyway. Use GPIO.setwarnings(False) to disable warnings.
GPIO.setup(22, GPIO.OUT)
Card detected
Card read UID(integer values): 77,84,46,59
Size: 8
Sector 0 Block 0 4d 54 2e 3b 0c 08 04 00 62 63 64 65 66 67 68 69
Sector 0 Block 1 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Sector 0 Block 2 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Sector 0 Block 3 00 00 00 00 00 00 ff 07 80 69 ff ff ff ff ff ff
Trailer !------keyA-----! !-access--! !-----keyB------!
Sector 1 Block 0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Sector 1 Block 1 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Sector 1 Block 2 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Sector 1 Block 3 00 00 00 00 00 00 ff 07 80 69 ff ff ff ff ff ff
Trailer !------keyA-----! !-access--! !-----keyB------!
Sector 2 Block 0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Sector 2 Block 1 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Sector 2 Block 2 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Sector 2 Block 3 00 00 00 00 00 00 ff 07 80 69 ff ff ff ff ff ff
Trailer !------keyA-----! !-access--! !-----keyB------!
Sector 3 Block 0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Sector 3 Block 1 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Sector 3 Block 2 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Sector 3 Block 3 00 00 00 00 00 00 ff 07 80 69 ff ff ff ff ff ff
Trailer !------keyA-----! !-access--! !-----keyB------!
Sector 4 Block 0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Sector 4 Block 1 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Sector 4 Block 2 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Sector 4 Block 3 00 00 00 00 00 00 ff 07 80 69 ff ff ff ff ff ff
Trailer !------keyA-----! !-access--! !-----keyB------!
Sector 5 Block 0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Sector 5 Block 1 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Sector 5 Block 2 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Sector 5 Block 3 00 00 00 00 00 00 ff 07 80 69 ff ff ff ff ff ff
Trailer !------keyA-----! !-access--! !-----keyB------!
Sector 6 Block 0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Sector 6 Block 1 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Sector 6 Block 2 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Sector 6 Block 3 00 00 00 00 00 00 ff 07 80 69 ff ff ff ff ff ff
Trailer !------keyA-----! !-access--! !-----keyB------!
Sector 7 Block 0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Sector 7 Block 1 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Sector 7 Block 2 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Sector 7 Block 3 00 00 00 00 00 00 ff 07 80 69 ff ff ff ff ff ff
Trailer !------keyA-----! !-access--! !-----keyB------!
Sector 8 Block 0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Sector 8 Block 1 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Sector 8 Block 2 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Sector 8 Block 3 00 00 00 00 00 00 ff 07 80 69 ff ff ff ff ff ff
Trailer !------keyA-----! !-access--! !-----keyB------!
Sector 9 Block 0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Sector 9 Block 1 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Sector 9 Block 2 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Sector 9 Block 3 00 00 00 00 00 00 ff 07 80 69 ff ff ff ff ff ff
Trailer !------keyA-----! !-access--! !-----keyB------!
Sector 10 Block 0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Sector 10 Block 1 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Sector 10 Block 2 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Sector 10 Block 3 00 00 00 00 00 00 ff 07 80 69 ff ff ff ff ff ff
Trailer !------keyA-----! !-access--! !-----keyB------!
Sector 11 Block 0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Sector 11 Block 1 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Sector 11 Block 2 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Sector 11 Block 3 00 00 00 00 00 00 ff 07 80 69 ff ff ff ff ff ff
Trailer !------keyA-----! !-access--! !-----keyB------!
Sector 12 Block 0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Sector 12 Block 1 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Sector 12 Block 2 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Sector 12 Block 3 00 00 00 00 00 00 ff 07 80 69 ff ff ff ff ff ff
Trailer !------keyA-----! !-access--! !-----keyB------!
Sector 13 Block 0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Sector 13 Block 1 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Sector 13 Block 2 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Sector 13 Block 3 00 00 00 00 00 00 ff 07 80 69 ff ff ff ff ff ff
Trailer !------keyA-----! !-access--! !-----keyB------!
Sector 14 Block 0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Sector 14 Block 1 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Sector 14 Block 2 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Sector 14 Block 3 00 00 00 00 00 00 ff 07 80 69 ff ff ff ff ff ff
Trailer !------keyA-----! !-access--! !-----keyB------!
Sector 15 Block 0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Sector 15 Block 1 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Sector 15 Block 2 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Sector 15 Block 3 00 00 00 00 00 00 ff 07 80 69 ff ff ff ff ff ff
Trailer !------keyA-----! !-access--! !-----keyB------!
Modified/New sources. Just add/overwrite these in the same directory.
- Read2.py
- tries to read blocks 0, 1 and 3 from sector 0 (printout says sectors 0, 1 and 3)
- Dump2.py
- the printout is formatted to show better the sectors and blocks, requires new MFRC522.py (see below)
- MFRC522.py
- the additional parts required by Dump2.py are added at the end of the file
Links
It is difficult to find good RFID overview articles or presentations. Good starting point is the excellent book RFID Handbook, 3rd Ed.
Security related aspects
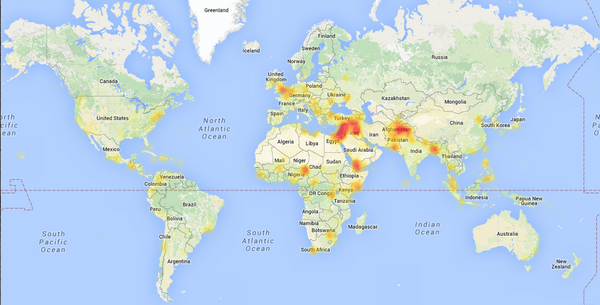
Hacking community has been active on RFID for some years.
There are some ways to protect your RFID cards.