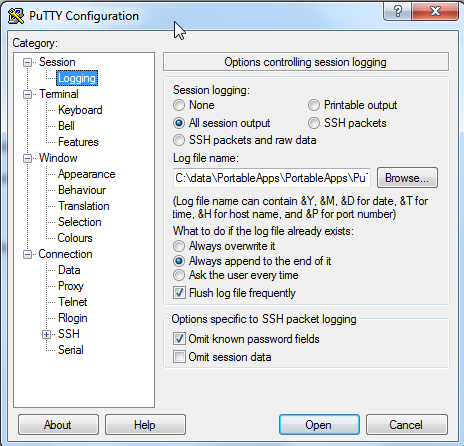
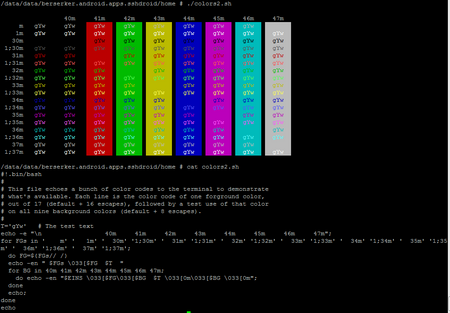
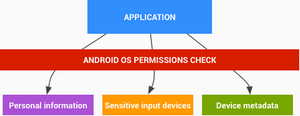
First, putty should be configured with “all session output”, see figure below. Next, the log file should contain some ANSI escape codes. For creating colors with the help of awk script, please see another blog.
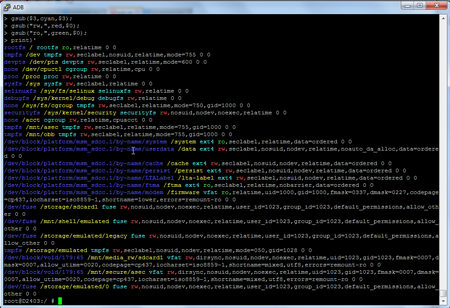
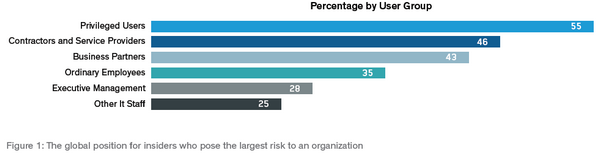
The text below is how the log file looks like. It contains the printout from the mount command.
I haven’t found a good way to get black background when using the GUI tool. With the command line tool, it is possible to use stylesheet to set the background color.
After saving the output into html, then one can modify the HTML <body> tag to get the background color, please see below:
Then execute the ansifilter command. If the log file is “mount.log” and output is mount.html, then command looks like this:
Please note that, the html output is now referring to that stylesheet as it add the following line to the html:
root@D2403:/ #
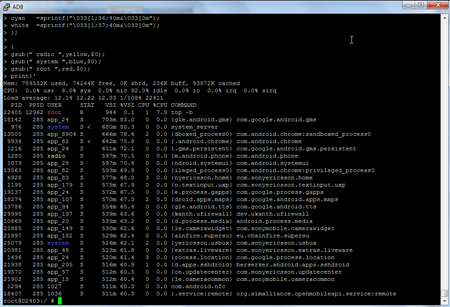
root@D2403:/ # mount | awk '
> BEGIN {IGNORECASE=1;
> black =sprintf("\033[1;30;40m&\033[0m");
> red =sprintf("\033[1;31;40m&\033[0m");
> green =sprintf("\033[1;32;40m&\033[0m");
> yellow =sprintf("\033[1;33;40m&\033[0m");
> blue =sprintf("\033[1;34;40m&\033[0m");
> purple =sprintf("\033[1;35;40m&\033[0m");
> cyan =sprintf("\033[1;36;40m&\033[0m");
> white =sprintf("\033[1;37;40m&\033[0m");
> };
>
> {
> gsub($1,blue,$1);
> gsub($2,yellow,$2);
> gsub($3,cyan,$3);
> gsub("rw,",red,$0);
> gsub("ro,",green,$0);
> print}'
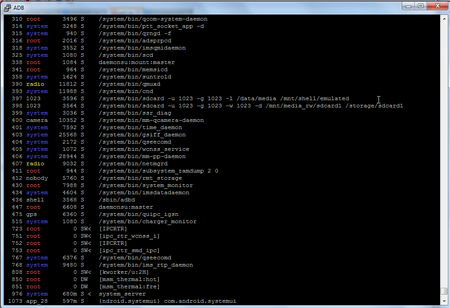
rootfs / rootfs ro,relatime 0 0
tmpfs /dev tmpfs rw,seclabel,nosuid,relatime,mode=755 0 0
devpts /dev/pts devpts rw,seclabel,relatime,mode=600 0 0
none /dev/cpuctl cgroup rw,relatime,cpu 0 0
proc /proc proc rw,relatime 0 0
sysfs /sys sysfs rw,seclabel,relatime 0 0
selinuxfs /sys/fs/selinux selinuxfs rw,relatime 0 0
debugfs /sys/kernel/debug debugfs rw,relatime 0 0
none /sys/fs/cgroup tmpfs rw,seclabel,relatime,mode=750,gid=1000 0 0
securityfs /sys/kernel/security securityfs rw,nosuid,nodev,noexec,relatime 0 0
none /acct cgroup rw,relatime,cpuacct 0 0
tmpfs /mnt/asec tmpfs rw,seclabel,relatime,mode=755,gid=1000 0 0
tmpfs /mnt/obb tmpfs rw,seclabel,relatime,mode=755,gid=1000 0 0
/dev/block/platform/msm_sdcc.1/by-name/system /system ext4 ro,seclabel,relatime,data=ordered 0 0
/dev/block/platform/msm_sdcc.1/by-name/userdata /data ext4 rw,seclabel,nosuid,nodev,relatime,noauto_da_alloc,data=ordered 0 0
/dev/block/platform/msm_sdcc.1/by-name/cache /cache ext4 rw,seclabel,nosuid,nodev,relatime,data=ordered 0 0
/dev/block/platform/msm_sdcc.1/by-name/persist /persist ext4 rw,seclabel,nosuid,nodev,relatime,data=ordered 0 0
/dev/block/platform/msm_sdcc.1/by-name/LTALabel /lta-label ext4 rw,seclabel,nosuid,nodev,relatime,data=ordered 0 0
/dev/block/platform/msm_sdcc.1/by-name/ftma /ftma ext4 ro,seclabel,relatime,nobarrier,data=ordered 0 0
/dev/block/platform/msm_sdcc.1/by-name/modem /firmware vfat ro,relatime,uid=1000,gid=1000,fmask=0337,dmask=0227,codepage=cp437,iocharset=iso8859-1,shortname=lower,errors=remount-ro 0 0
/dev/fuse /storage/sdcard1 fuse rw,nosuid,nodev,noexec,relatime,user_id=1023,group_id=1023,default_permissions,allow_other 0 0
/dev/fuse /mnt/shell/emulated fuse rw,nosuid,nodev,noexec,relatime,user_id=1023,group_id=1023,default_permissions,allow_other 0 0
/dev/fuse /storage/emulated/legacy fuse rw,nosuid,nodev,noexec,relatime,user_id=1023,group_id=1023,default_permissions,allow_other 0 0
tmpfs /storage/emulated tmpfs rw,seclabel,nosuid,nodev,relatime,mode=050,gid=1028 0 0
/dev/block/vold/179:65 /mnt/media_rw/sdcard1 vfat rw,dirsync,nosuid,nodev,noexec,relatime,uid=1023,gid=1023,fmask=0007,dmask=0007,allow_utime=0020,codepage=cp437,iocharset=iso8859-1,shortname=mixed,utf8,errors=remount-ro 0 0
/dev/block/vold/179:65 /mnt/secure/asec vfat rw,dirsync,nosuid,nodev,noexec,relatime,uid=1023,gid=1023,fmask=0007,dmask=0007,allow_utime=0020,codepage=cp437,iocharset=iso8859-1,shortname=mixed,utf8,errors=remount-ro 0 0
/dev/fuse /storage/emulated/0 fuse rw,nosuid,nodev,noexec,relatime,user_id=1023,group_id=1023,default_permissions,allow_other 0 0
root@D2403:/ # exit
root@D2403:/data/data/berserker.android.apps.sshdroid/home # exit