In an earlier blog, a GUI tool called WinMD5 was recommended for maintaining integrity of your files. However, hash calculation based on SHA-512 is more security nowadays.
For example, if you need to proof to others, that you possessed a certain file (ie. evidence), then at least 2 things are needed:
-
better fingerprinting, ie. hash calculation (this blog)
-
signed timestamp from third party (see another blog )
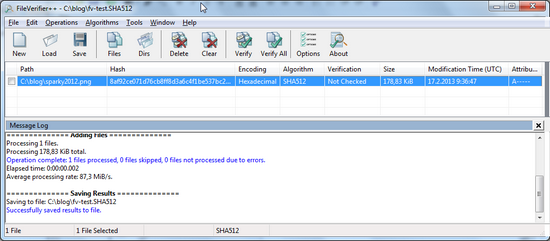
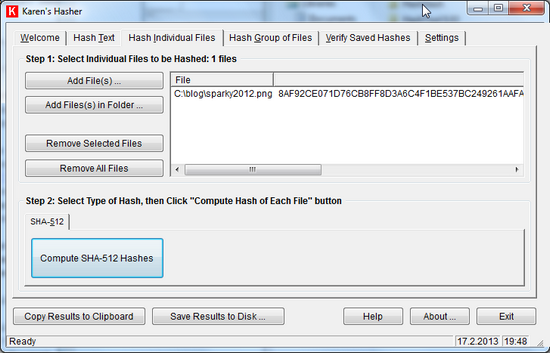
In this blog especially 2 open source GUI tools with SHA-512 hash calculation are mentioned, FileVerifier++ and Karen’s Hasher .
Wikipedia:
A cryptographic hash function is a hash function; that is, an algorithm that takes an arbitrary block of data and returns a fixed-size bit string, the hash value, such that any change to the data will change the hash value. In information security contexts, cryptographic hash values are sometimes called (digital) fingerprints, checksums, or just hash values.
Tools
-
Open source, just unpack, no installation needed
-
Drag&Drop
-
Files, Folders, Verify, store hashes into file
-
Open source, installation needed
-
File, Folder, Verify, store hashes into file or clipboard
Other Hash Tools
-
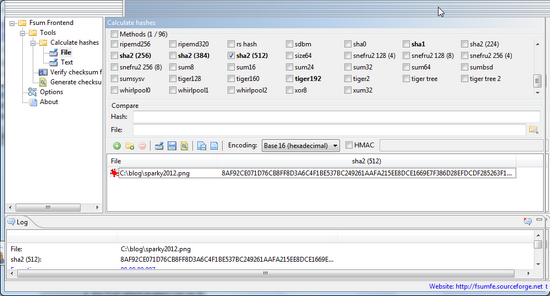
Fsum Frontend (and FSUM )
-
Files, Folders, Verify, store hashes into file
-
-
-
Open source
-
Single File
-
-
-
Open source
-
Single file, verify
-
-
HashCalculator
-
Open source
-
Single file, copy hash to clipboard
-
- HashSlash
-
-
Drag&Drop
-
Single File, copy result without file name into clipboard
-
- MultiHasher
- portable
- ComputeHash
- Integrated with explorer, right mouse button menu
- single file, copy hash into file or clipboard
Links
-
SHA details at NIST