Are you sharing or producing photos, images, music, videos, programs, documents or anything else and you are concerned on how to proof that your work is yours?
First of all, you need to be able to show that you really possessed the file or files at a certain time. The typical way of doing that is to create a fingerprint (mathematical hash ) of your file, and get that fingerprint (hash) timestamped by a trusted third party.
Fingerprint (hash) is unique and shows that only a file with certain contents (sequence of bits) can have produced this fingerprint value. And since you have no control over the third party’s time, nor over their signed timestamp, then you have no ways to modify the timestamp after it has ben created for your file. Therefore you can show that you really had the certain file in your possession at certain time.
It is possible to run your own timestamp server and provide signing service with timestamp to your organization, but that is another story. In this blog, the focus is photographers and musicians who wish to protect their own work.
Wikipedia:
According to the RFC 3161 standard, Trusted timestamp is a timestamp issued by a trusted third party (TTP) acting as a Time Stamping Authority (TSA). It is used to prove the existence of certain data before a certain point (e.g. contracts, research data, medical records,…) without the possibility that the owner can backdate the timestamps.
Free service example 1, protecting single vulnerable file “sparky2012.png”
Case: The photo, file “sparky2012.png”, is shared online (see below).
Step 1: Calculate hash
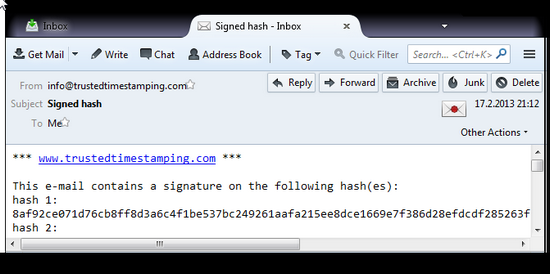
The SHA-512 hash is calculated with FileVerifier++ tool (see earlier blog ). The result is shown below.
; Created with FileVerifier++ v0.6.3.5830 8af92ce071d76cb8ff8d3a6c4f1be537bc249261aafa215ee8dce1669e7f386d28efdcdf285263f11bc453c4049b9defc11f3045aacd0c59a87609a81a62ace2 *C:\blog\sparky2012.png
Step 2: Ask for signed timestamp
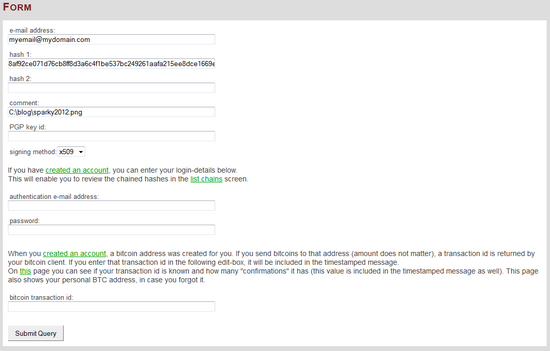
In this example, www.trustedtimestamping.com is used as trusted third party. On their site, there is a form, where one can fill in 2 different hash values, a comment field, and a return address there to receive the signed timestamp (see below).
In few minutes, the signed email is sent to your email box.
Step 3: Archive the proofs
Many online tools has limitations with signed emails. Therefore it is better to access those emails via a desktop client like Thunderbird.
Since the trustedtimestamping.com has certificate from COMODO, then one need to define COMODO as trusted Authority if one would like Thurderbird to show “sing verification ok” for the email. The COMODO certificate is available via web link. One can save this into a file, and then import into Thurderbird.
If wished, one can import the COMODO certificate via following menu choises: Tools -> Options -> Advanced -> Certificates -> View Certificates -> Authorities -> Import
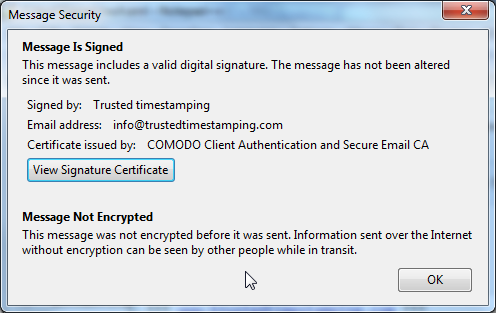
After this “the envelope seal” looks fine in the email reading mode, see below.
By clicking on the envelope, then more details are visible. ie. email is signed by “Trusted timestamping” and certificate that they are using originates from COMODO. The details also show that “message has not been altered”.
One can save the received signed email into a local file (*.eml).
For the proof, one need to archive following files:
- sparky2012.png
- containing the shared photo
- sparky2012.SHA512
- containing the hash of photo
- sparky2012-timestamp.eml
- containing the signed timestamp from trusted third party
Notes:
- Only one free service is presented here. However, this method is more tedious than with the commercial counterparts. There are more free services available, but remember that when looking for free alternative, the solution quality, suitability and reliability might cause issues.
- For serious work, please evalute the commercial solutions in order to find the most suitable for you purposes. However, with free alternatives, one can achieve much better proof than “your word only”.
Improvements
- Approach, “hash value sepated from timestamp process”, weakness
- Weakness: someone could always claim that you have copied the hash value from somewhere else. And it is only later that you got the file itself. After all, SHA-512 could have been calculated by someone else.
- Mitigation: Include in the timestamp request something that is depending on the file content and that is something that only you know. You can encrypt the file with the password, or private key, that only you have access to, and then include the SHA-512 of that encrypted file as hash 2. Toucan is one alternative for encrypting a single file (see blog). Naturally you need to include these additional part in your archive.
Free service example 2, protecting secure container
Instead of requesting timestamp for every singe file, it is more efficient and secure to timestamp a secure container. Here secure container means an archive which contains many files inside and are accessable only via password or private key. Examples are password protected zip file and a Truecrypt container (*.tc).
By timestamping the secure container, one is basically timestamping all the content of that container. For example all the photos inside. Naturally one need to archive the full container instead of single shared files.
Easier way, using commercial solution
It is a challende to choose the best solution for your case, since there are several tools available for creating timestamped fingerprints of your documents. In many cases they are focussed on Microsoft Office and Adobe PDF documents. And in some cases your own certificate can be used in the process providing even more proof that you were involved in this process. In some cases the payment is per timestamp operation, while in some solutions the payment is per year, or one time payment only. The possible combinations varies a lot depending on the details and type of documents that can be protected.
Many of these do offer evaluation period. Some links to companies and solutions are:
- https://www.universign.eu/en/
- http://www.aloaha.com
- http://www.verisign.com/
- http://www.ascertia.com
- http://easytimestamping.com
- http://www.ica.cz/English
- https://www.globalsign.com
- http://www.comodo.com
- http://www.trustcenter.de
- http://www.surety.com
- http://www.digistamp.com
- http://www.cacert.org/
- http://www.proofspace.com/