There are videos available from 2010 in youtube.
Presentation by Lars Söderlund, Alliansor AB
– he is teacher at Swedish Standards Institute SIS
Other link to SIS: Information sequrity management systems
There are videos available from 2010 in youtube.
Presentation by Lars Söderlund, Alliansor AB
– he is teacher at Swedish Standards Institute SIS
Other link to SIS: Information sequrity management systems
There exist an interesting model for measuring Software Security called BSIMM.
Their Software Security Framework covers 4 domains and 12 practises.
The maturity is described with levels, and one can compare own result agains the average.
Main links
freeFTPd is good alternative when you need to transfer big amount of traffic over local network.
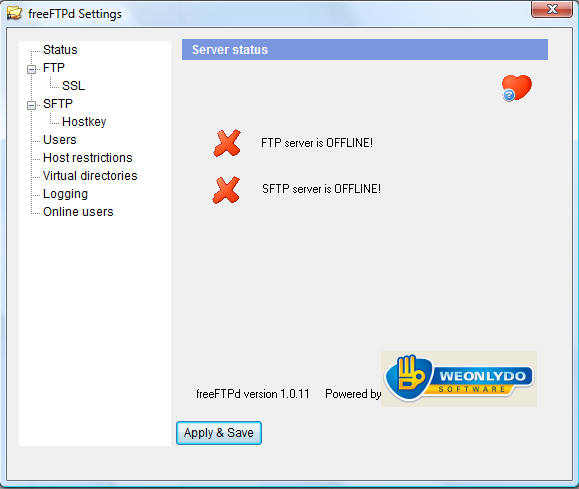
During installation, it gives option to run as a service. But an as easy alternative is to start it manually whenever you need to use it.
SFTP is the preferred way, and is supported by many clients (for example WinSCP). With freeFTPd-WinSCP tools one can perform secure file transfers adhoc.
I have used some free & open java ftpd tools earlier, but freeTFPd is much faster.
There exist several notes keeping and personal organizer type of programs.
KeyNote NF is one of these programs.
I’m using Beta version (1.7.9), and main features which I like most:
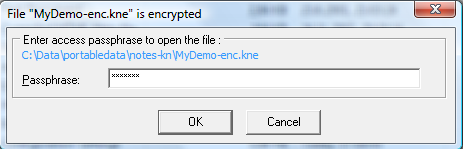
If opening encrypted file, it will ask for password
Note 1
The installation is by uncmpressing the file. Upgrade is done by copying “keynote.exe” into installation directory.
Note 2
The default suffix is “*.knt”. However in Vista+, one might need to start the program “Run as Administrator” ir order for the suffix registration to work.
Update 2016-05-12: This is now archived, I’m currently using CherryTree
MyEnTunnel is tool which
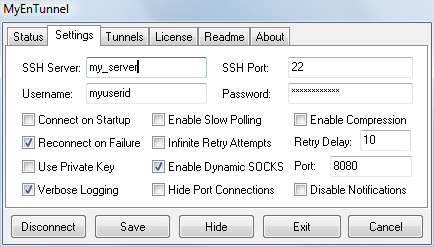
MyEnTunnel can be used as substitute for the bat file mentioned in privacy and internet communication blog.
After installation, the installation directory can be copied into portable device. ie. i is portable.
Every day there are all kind of privacy related information flowing in and out our computers (figure below).
We might be using physical connection at our home and be connected via our ISP (Internet Service Provider). Or when travelling, we might be using unsecured open wifi connection from an unknown ISP.
Sometimes we might wonder who else can have access to our data, or who else could be seeing what we do in internet. How one can know, if someone is monitoring your communication?
Even though if there are security policies in place, then how one can really know?
And who is watching those who have access to monitoring? For example, in some residential areas, the internet might be shared between households. The question then is that how much your neighbour, who owns the internet access point, can monitor the communication.
We might be signing for new managine, and during registration and payment processes we provide details of our identity. Later, we use the same tools for accessing other sites in the internet. For example joining a new social network.
There is information which we are knowingly sending and receiving. In addition, there is information that is beyond our immediate control. This information is controlled by the systems and applications which we are using (figure below).
There are solutions to protect communication. The one presented here is using 3 components (figure below):
There exist several instructions in internet on how to use Firefox and putty to protect your communication.
For example, how to configure putty and firefox, see here.
In addition, dns request from firefox can be routed to the same secure communication, see here.
Putty: In Connection->SSH->Tunnels define port number like 8080 in “Source port”, and as type select “Dynamic”.
Firefox: Define Manual proxy as: SOCKS host 127.0.0.1 with port 8080
Then write phrase “about:config” as URL in order to enter additional options page. Define yes for option “network.proxy.socks_remote_dns”
Some programs, for example some email notifiers, do not support SOCKS. Luckily there exist tools for those situations. For example FreeCap can be used as SOCKS client.
There are 2 concerns left, even when using secure communication up to your ssh server:
For the first one, there are several commercial anonymizer services available. Or if you are lucky, you might have access to a public organization which provides this type of service to their members.
For the second, at minimum one should consider which application you are using to access which type of site. For browsing only, there exist several privacy oriented browsers which limit the storage and transfer of application information (cache, cookies, temporary files etc.).
One can use a site like http://showip.net to see your current public IP address. It also shows your location on a map (based on your IP address).
Please note, that this technique presented here might be forbidden in company security policy, even if it is not prevented. This is because the same technique can be used to access malicious sites, and company’s security controls are not working any more as they should. Uncontrolled access to malicious sites can cause harm not only to company’s computer, but to business as well.
putty contains a command line version called plink. With plink, it is possible to create new protection connection to ssh server with “one click”. 2 files are needed, one to execute plink command with right parameters, and other file for ssh commands to be executed on ssh server in order to keep the connection active.
activate-ssh.bat contains
C:’my_path’plink -D 8080 -pw my_ssh_password -C -m ssh-commands.txt -ssh my_userid@my_ssh_server
ssh-commands.txt contains bash shell commands
bash
while 1
do
date
done
Advanced usage, alternative
There exist an alternative called MyEnTunnel, which can be use instead (blog). It is more user friendly and easier to use and setup.
For firefox, there exist proxy switcher plugins, which are helpfull if using this technique often.
Xming is an X Server which one might need when working with unix systems.
It is claimed to be portable as well (I haven’t tried the portable part).
Configuration is done by a wizard (below).
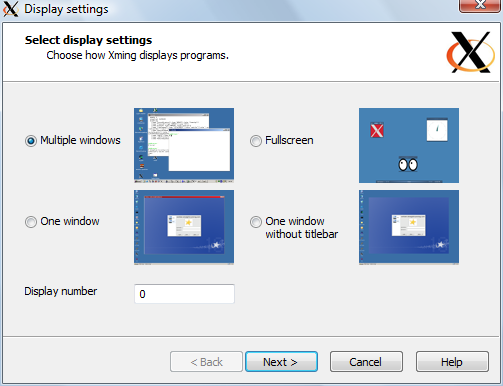
Wizard also gives option to define where to connect, and which program to open at connection (like xterm below). Wizard also asks about clipboard sharing, which makes it easier to operate unix from MS windows. (Clipboard issues are common in cross platform operations).
If using Multiple windows, then one can open individual windows for each remote program. When using Fullscreen, one would also a X Window Manager program to manage windows. (Most system do have xkill program, which might be helpfull to remove windows when no window manager is running. When there is no window manager, then one cannot close or move windows 🙂 )
xclock is the other commonly available program to test your X Windows when logging into new system.