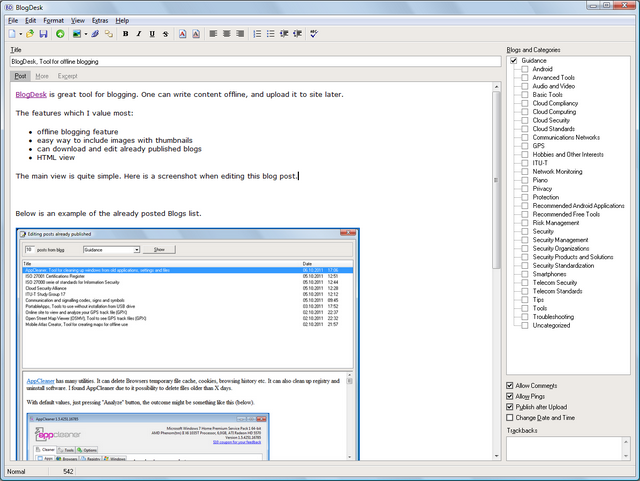
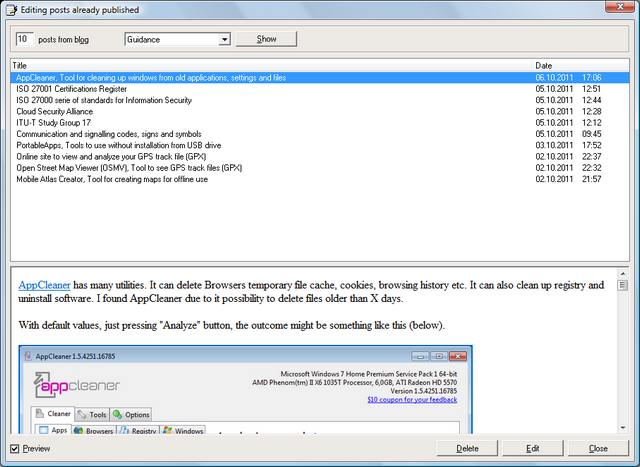
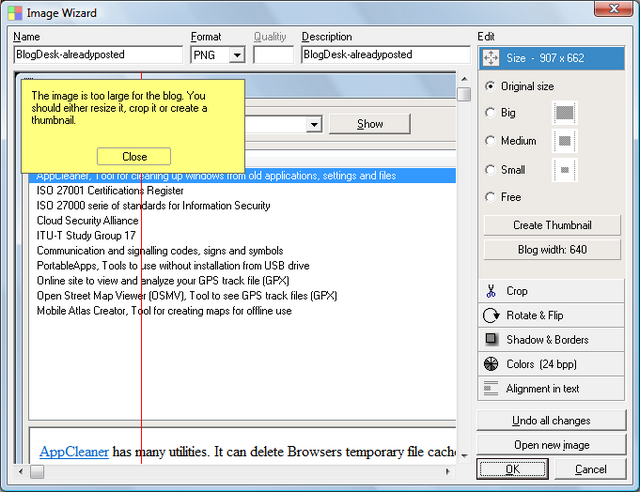
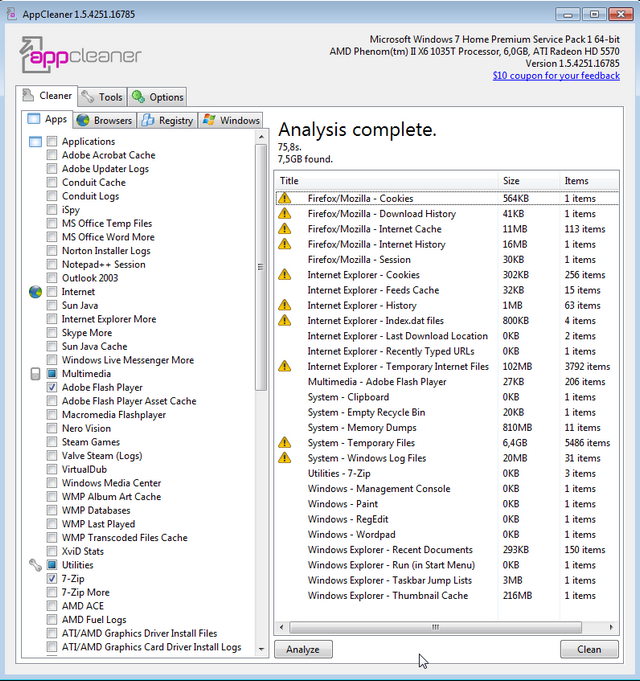
I just recently bought a type of KVM switch with USB and audio cables, and it is just great. For an example, see Dlink KVM-221 below.
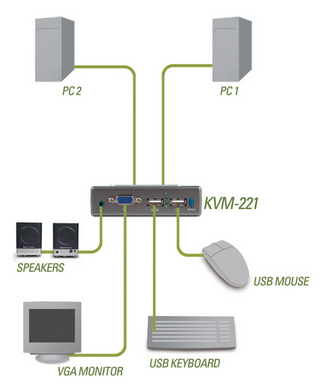
No more moving laptop around the table when needed. Now, with one switch button, I can switch between dektop and laptop computers. And keep on using the same keyboard, mouse, monitor and headphones!
One more good thing, there is no need for external power supply. KVM takes power from USB connection.
I bought mine from Clas Ohlson, and it turned out to be one model of the Wiretek. My model looks quite close to this (below).