ENISA has published exercise material for people working in CERTs (Computer Emergency Response Team).
First set of material is related to CERT organizations.
- Setting-up Guide
- CERT Running Guide
- Baseline capabilitites for national / governmental CERTs
- Good Practice Guide for Incident Management
- Proactive detection of network security incidents
- information exchange between CERTs
- Incident Handling Tools
Second set of material is exercises
- Exercises Handbook for teacher
- Exercises Toolset for student
- Live DVDs
- CSIRT Exercise Handbook for teacher
- CSIRT Exercise Toolset for student
- CSIRT Exercise Netflow for student
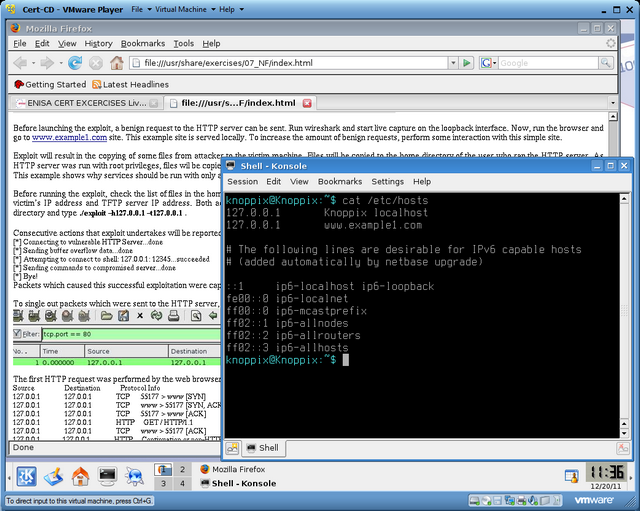
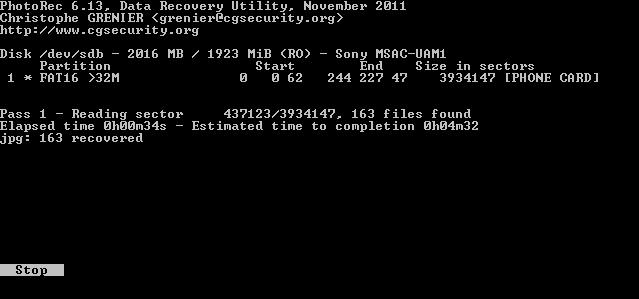
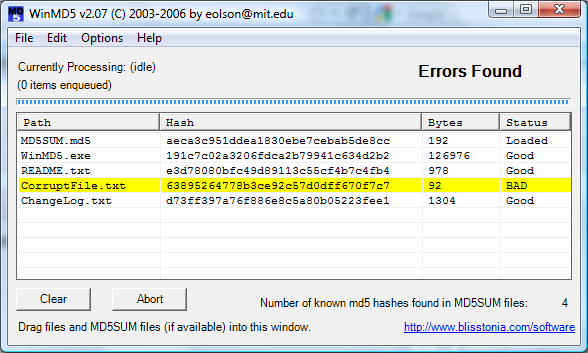
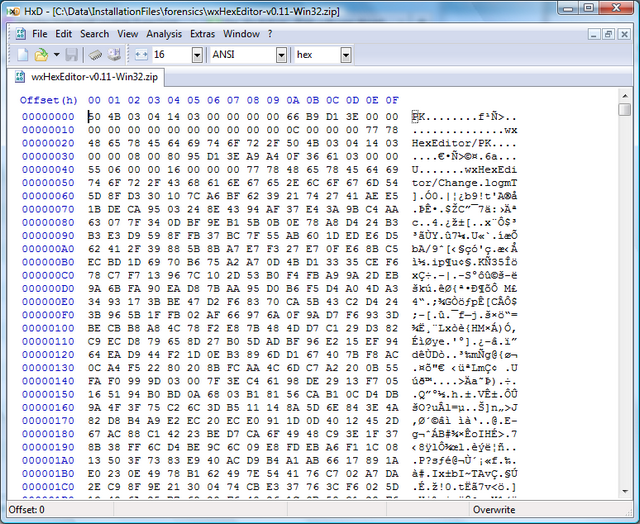
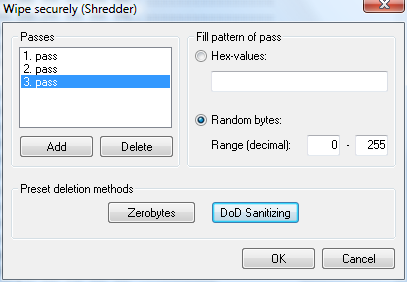
The figure below shows live DVD executed inside VMware player. Task 7 comes with examples.
The list is exercises:
- Exercise 1: Triage and Basic Incident Handling
- Exercise 2: Incident Handling Procedure Testing
- Exercise 3: Recruitment of CERT Staff
- Exercise 4: Developing CERT Infrastructure
- Exercise 5: Vulnerability Handling
- Exercise 6: Writing Security Advisories
- Exercise 7: Network Forensics
- Exercise 8: Establishing External Contacts
- Exercise 9: Large-scale Incident Handling
- Exercise 10: Automation in Incident Handling
- Exercise 11: Incident Handling in Live Role Playing
- Exercise 12: Cooperation with Law Enforcement Agencies