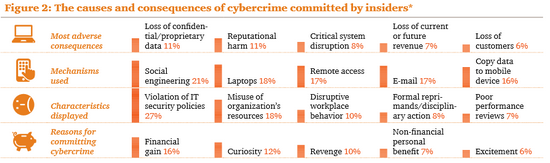
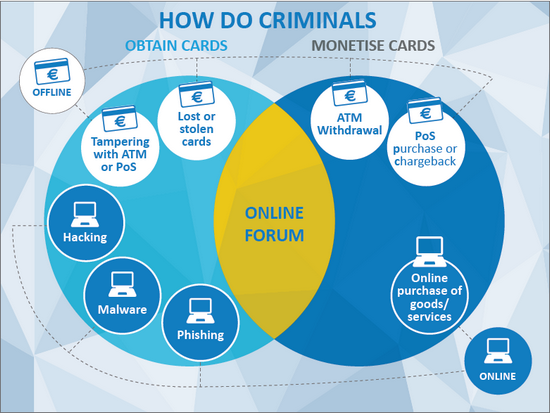
EC3 (European Cybercrime Centre at Europol) has published a good report on the cybercrime, worth to take a look. The other report by McAfee complements with estimations of the costs.
Definitions
TechTarget: Cybercrime is a term for any illegal activity that uses a computer as its primary means of commission.
IT Law Wiki: Cybercrime is criminal activities that specifically target a computer or network for damage or infiltration and also refers to the use of computers as tools to conduct criminal activity
Oxford: Criminal activities carried out by means of computers or the Internet.
ISO 27032: criminal activity where services or applications in the Cyberspace are used for or are the target of a crime, or
where the Cyberspace is the source, tool, target, or place of a crime.the Cyberspace: complex environment resulting from the interaction of people, software and services on the Internet by means
of technology devices and networks connected to it, which does not exist in any physical form.
iOCTA (Internet Organised Crime Threat Assessment )
Selected extracts from the report (2014 pdf):
The Crime-as-a-Service (CaaS) business model drives the digital underground economy by providing a wide range of commercial services that facilitate almost any type of cybercrime.
The anonymisation techniques used in parts of the Internet, known as Darknets, allow users to communicate freely without the risk of being traced.
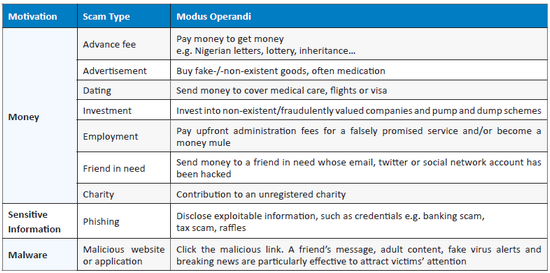
Social engineering related confidence tricks (scams)
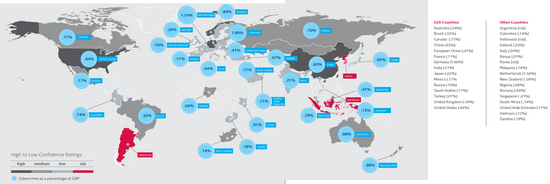
Global Cost of Cybercrime
Selected extracts from “Net Losses: Estimating the Global Cost of Cybercrime“
Comparing cost of cybercrime with other costs.
|
Activity |
Cost As % of GDP |
|
Maritime Piracy |
0.02% (global) |
|
Transnational Crime |
1.2% (global) |
|
Counterfeiting/Piracy |
0.89% (global) |
|
Pilferage |
1.5% (US) |
|
Car Crashes |
1.0% (US) |
|
Narcotics |
0.9% (global) |
|
Cybercrime |
0.8% (global) |
Showing estiamated cost for some countries.
Other Links
- Budapest Convention on Cybercrime, in wikipedia,
- Annual reports at the IC3 (Internet Crime Complaint Center)
- 2014 US State of Cybercrime Survey (by PwC)
- A Brief History of Malware and Cybercrime
- Spam, Rootkits, Viruses, Computer intrusions,