After few years, even after little use, my Lacie 1000 Gb NAS went broken. When powering it up, the hard disk did not spin, but a smoke started to come up from the back side of the box close to the power cord. The power connector melted, but there were no other visual damage.
The only way to recover files was to take the hard drive out from the box and get it directly connected with a PC. Luckily I had an USB to SATA adapter, so the connection was easy. When connecting it into a windows 10 machine, it showed that the USB drivers were working fine, but there were no new hard drive available. The figure below shows the opened NAS box on the right, and the detached hard drive on the center. (The usb drive on the left is to make the backup into that one.)

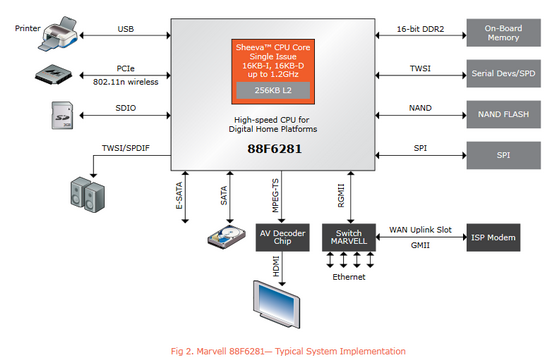
After a little search, the reason became clear: this model has a ARMv5 compatible SoC (System on Chip) which can run linux and that the filesystem in the drive is most propably xfs (ie. not recognized by Windows OS) . In this device, the CPU is 88F6281, which seems suitable for these NAS devices.
And then after connecting the drive into xubuntu linux in VirtualBox, then files became accessable:-)
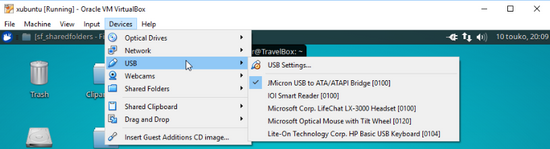
The other USB drive was also connected to the same xubuntu, after which it was possible to copy the files. The printout below shows the xfs for sdb2 (NAS disk) and ntfs for sdc1 (USB drive).
traveler@TravelBox:~$ sudo lsblk -o NAME,FSTYPE,SIZE,MOUNTPOINT,LABEL
NAME FSTYPE SIZE MOUNTPOINT LABEL
sda 8G
+-sda1 ext4 6,5G /
+-sda2 1K
+-sda5 swap 1,5G
+-cryptswap1
swap 1,5G [SWAP]
sdb 931,5G
+-sdb1 1K
+-sdb2 xfs 929,6G /media/traveler/537daead-0d83-
+-sdb5 swap 251M
+-sdb6 7,8M
+-sdb7 linux_ra 7,8M
+-sdb8 linux_ra 831,5M
+-sdb9 ext3 855M /media/traveler/2f3bc6b9-d96a-
+-sdb10 7,8M
sdc 1,8T
+-sdc1 ntfs 1,8T /media/traveler/Seagate Backup Seagate Backup Plus Drive
sr0 1024M
Other Links
-
-
-
-
NAS in wikipedia has a sentence like “
Many of these home consumer devices are built around ARM, PowerPC or MIPS processors running an embedded Linux operating system.“